Which statement is true when working with correlation IDS?
A Mule application need to invoice an API hosted by an external system to initiate a process. The external API takes anywhere between one minute and 24 hours to compute its process.
Which implementation should be used to get response data from the external API after it completes processing?
Refer to the exhibit.
What is the result of the Mule Maven Plugin configuration of the value of property its,keystorePassoword in CloudHub 2.0?

A custom policy needs to be developed to intercept all cutbound HTTP requests made by Mule applications.
Which XML element must be used to intercept outbound HTTP requests?
Refer to the exhibit.
What action must be performed to log all the errors raised by the VM Connector?
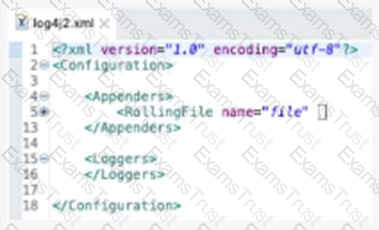
Refer to the exhibit.
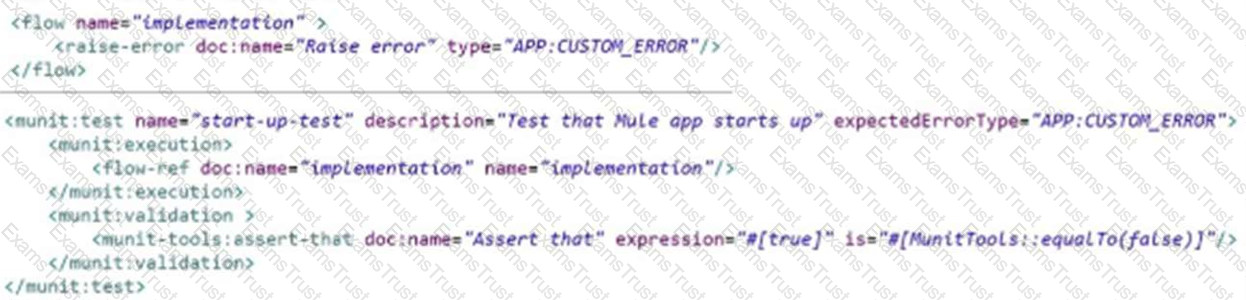
The flow name is ‘’implementation’’ with code for the MUnit test case.
When the MUnit test case is executed, what is the expected result?
In a Mule project, Flow-1 contains a flow-ref to Flow-2 depends on data from Flow-1 to execute successfully.
Which action ensures the test suites and test cases written for Flow-1 and Flow-2 will execute successfully?
A system API that communicates to an underlying MySQL database is deploying to CloudHub. The DevOps team requires a readiness endpoint to monitor all system APIs.
Which strategy should be used to implement this endpoint?
A Mule application for processing orders must log the order ID for every log message output.
What is a best practice to enrich every log message with the order ID?
A Mule implementation uses a HTTP Request within an Unit Successful scope to connect to an API.
How should a permanent error response like HTTP:UNAUTHORIZED be handle inside Until Successful to reduce latency?
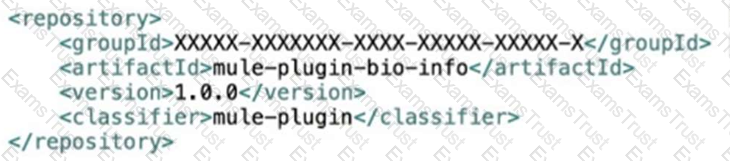
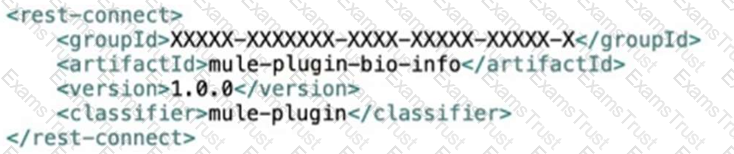
Refer to the exhibits.
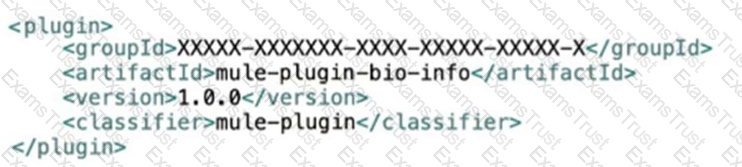
Bioinfo System API is implemented and published to Anypoint Exchange. A developer wants to invoke this API using its REST Connector.
What should be added to the POM?
A)
B)
C)
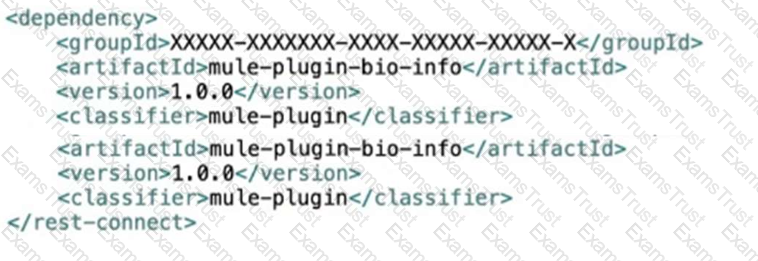
D)

E)
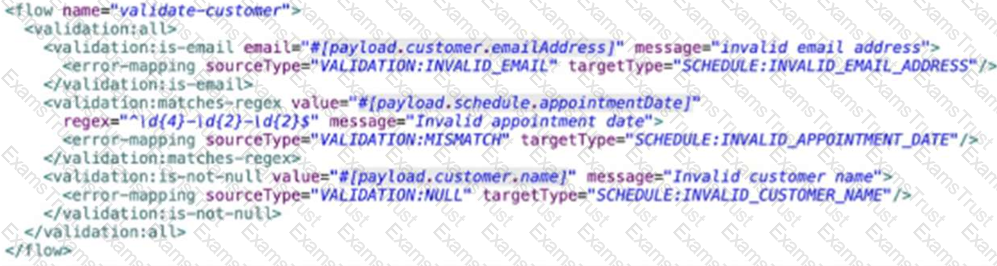
An API has been built to enable scheduling email provider. The front-end system does very little data entry validation, and problems have started to appear in the email that go to patients. A validate-customer’’ flow is added validate the data.
What is he expected behavior of the ‘validate-customer’’ flow?
Which type of cache invalidation does the Cache scope support without having to write any additional code?
A heathcare customer wants to use hospital system data, which includes code that was developed using legacy tools and methods. The customer has created reusable Java libraries in order to read the data from the system.
What is the most effective way to develop an API retrieve the data from the hospital system?
Which statement is true when using XML SDK for creating custom message processors?
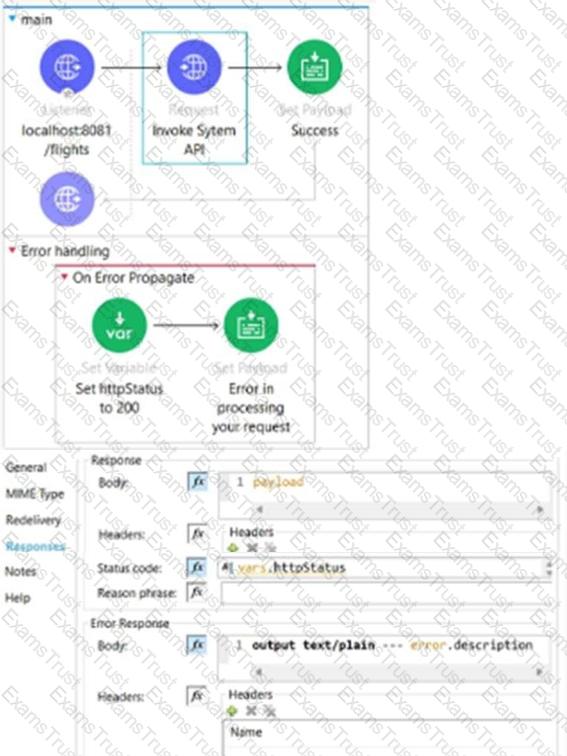
The HTTP Request operation raises an HTTP CONNECTIVITY error.
Which HTTP status code and body are returned to the web client?
Which pattern should be used to invoke multiple HTTP APIs in parallel and roll back failed requests in sequence?
A company has been using CI/CD. Its developers use Maven to handle build and deployment activities.
What is the correct sequence of activities that takes place during the Maven build and deployment?