Which of the following is required for a MID Server to have access to automatically stay up-to-date with instance versions?
When installing a MID Server on a Windows platform, which right must be associated when creating a Service Account?
Which of the following choices explain differences between Service Mapping and Discovery? (Choose two.)
As a first step in horizontal discovery, which of the following is where the Shazzam probe is placed in a request?
File-based Discovery is triggered during the .
From an SNMP Query pattern operation, which of the choices are valid Variable Types? (Choose two.)
If the WMI service is not running on a host, it will prevent the discovery of which devices?
Which of the below choices are needed for Quick Discovery? (Choose two.)
Which of the following describes the recommended permission level for credentials to discover Windows Servers?
What does the MID Server need to collect vCenter events?
With multiple CI data sources, which choice is the best for determining which source can update a CI attribute?
Which of the choices are types of temporary variables in a discovery pattern?
Choose 2 answers
Which of the below choices are kinds of variables used in discovery patterns? (Choose three.)
What pattern operation allows the transfer of a file from the MID Server to a target?
During the Discovery process, what determines if an Asset record is created?
In Discovery, what table associates an IP address and a credential?
Which choice best describes how to use a Behavior for discovery?
Based on this image, which of the following choices is true?
What is found on the far-right section of the Pattern Designer for horizontal patterns? (Choose two.)
Which of the following best describes what may also be required when increasing the max number of threads for a MID Server?
Which of the below choices are possible options under ACTION ON ALL in the Recommended Actions pane for an Automated Error Messages list within Discovery > Home?
Choose 2 answers
Which metrics comprise the Completeness KPI for CMDB Health? (Choose two.)
What role is needed by the MID Server's user account to interact with a ServiceNow instance?
Which of the below choices are benefits of Tracked Configuration Files? (Choose two.)
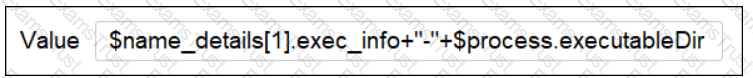
Which choice allows the following functionality to occur?
If this value is set to 1000 and a discovery must scan 10,000 IP addresses using a single MID Server, it creates 10 Shazzam probes with each probe scanning 1000 IP addresses.
By default, which of the following are automatically available as variables for horizontal discovery patterns? (Choose two.)
For what is File Based Discovery used?
Which method for deleting specific CIs is not discovered in 30 days?
Which of the following must be configured to allow a MID Server to access servers using WinRM?
Which choice best describes a horizontal discovery pattern?
Which choice will populate the Location field for a discovered CI?
What is the default thread count for a MID Server?
What entry point type must a horizontal pattern have to execute from a process classifier?