What is the maximum distance between two 8 Gb FC ports that can be connected using 50 µOM3 grade multimode fiber cable?
You are provisioning storage to a host with multipathing software installed and correctly configured. You discover that there are four paths to LUNs instead of the expected eight paths.
Why does this happen?
You need to merge two existing FC fabrics. After connecting the ISL to join the fabrics, numerous switches segment.
What should be done to prevent the segmentation?
Click the Exhibit button.
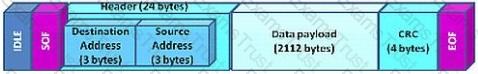
Which protocol is represented by the frame shown in the exhibit?
You have determined that the root cause of your problem is related to invalid characters being intermittently transmitted on your 4 Gb FC link.
What describes this condition?
Click the Exhibit button.
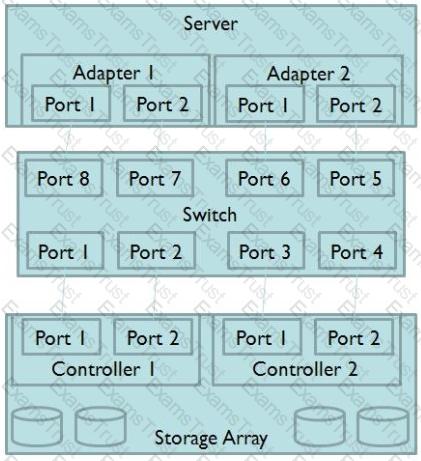
Referring to the exhibit, what are the two largest risks to a highly available solution? (Choose two.)
Click the Exhibit button.
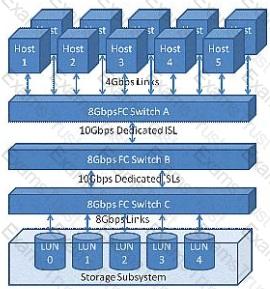
The customer configuration shown in the exhibit is not meeting the throughput needs of a newly installed application. The application's I/O profile consists of 100% 4 kilobyte reads and all servers require a sustained bandwidth of 150 MBps.
Which location within the configuration presents a performance bottleneck?
A new server needs to start from LUN 1 instead of LUN 0.
Which HBA setting must be configured?
Which two high availability elements can be achieved by remote storage replication? (Choose two.)
A colleague asks you if the added cost of using encrypting tape drives and sending the tapes off-site is warranted, since your IT organization already has large security investments such as firewalls and database table encryption.
What is your response?
You have received an emergency call from the night shift after they attempted to merge three small SANs in the engineering department. Once completed, all devices in SANs A and B communicate with one another but SAN C could not communicate with either of the other SANs because the fabric has become segmented.
Which statement is correct?
When troubleshooting an issue on a host, you discover that the existing file system partition has been corrupted after you provisioned a LUN to another host connected to the same FC fabric.
What is the cause of this problem?
You have twelve 500 GB drives and you need to provide two LUNs using RAID 6 protection for a customer.
What will be the size of each LUN?
You want to prevent unauthorized switches from connecting to your company's fabrics.
What should you do?