Which statements are true of Alliance Messaging Hub (AMH)? (Select the correct answer)
•Connectivity
•Generic
•Products Cloud
•Products OnPrem
•Security
AMH is highly resilient, and can consist of multiple instances and sites in parallel
AMH provides advanced integration capabilities
AMH is a messaging interface able to connect to other financial networks, not only SWIFT
All of the above
Alliance Messaging Hub (AMH) is a SWIFT product designed as a centralized messaging platform for financial institutions, enabling them to manage multiple messaging flows, including SWIFT and non-SWIFT networks. Let’s evaluate each statement:
•Statement A: AMH is highly resilient, and can consist of multiple instances and sites in parallel
This is true. AMH is designed for high availability and resilience, supporting deployments across multiple instances and sites to ensure continuity of operations. This capability is critical for large financial institutions handling high volumes of transactions. SWIFT documentation highlights AMH’s ability to operate in a distributed architecture, with instances running in parallel across primary and backup sites. This aligns with CSCF Control "1.1 SWIFT Environment Protection," which emphasizes the need for resilient infrastructure to prevent disruptions in the SWIFT environment.
•Statement B: AMH provides advanced integration capabilities
This is true. AMH offers advanced integration features, allowing institutions to connect various back-office systems, payment engines, and other financial applications to a single hub. It supports multiple message standards (e.g., SWIFT MT, ISO 20022) and provides transformation and routing capabilities, making it a versatile integration platform. This is a key selling point of AMH, as noted in SWIFT’s product documentation, enabling seamless interoperability across diverse systems.
•Statement C: AMH is a messaging interface able to connect to other financial networks, not only SWIFT
This is true. AMH is not limited to SWIFT messaging; it can connect to other financial networks, such as domestic payment systems, real-time gross settlement (RTGS) systems, or proprietary networks. AMH acts as a universal messaging hub, supporting multiple protocols and standards beyond SWIFT’s ecosystem (e.g., FIX for securities trading). This capability is well-documented in SWIFT’s AMH product overview, positioning it as a flexible solution for institutions with diverse connectivity needs.
•Statement D: All of the above
Since all three statements (A, B, and C) are true, this option is the correct answer. AMH’s design for resilience, advanced integration, and multi-network connectivity makes it a comprehensive messaging solution.
Summary of Correct Answer:
All statements about AMH are true, making "All of the above" (D) the correct choice.
References to SWIFT Customer Security Programme Documents:
•SWIFT Customer Security Controls Framework (CSCF) v2024: Control 1.1 emphasizes resilience, which AMH supports through its architecture.
•SWIFT Alliance Messaging Hub Documentation: Highlights AMH’s multi-site resilience, integration capabilities, and support for non-SWIFT networks.
•SWIFT Product Overview: Describes AMH as a universal messaging hub for SWIFT and other financial networks.
========
The Physical Security protection control is also aimed at protecting the “on call” and “working from home” employees’ equipment used to access the Swift-related components.

TRUE
FALSE
This question pertains to Control 7.3 – Physical Security in the CSCF:
Step 1: Control 7.3 Overview
Control 7.3 focuses on “physically securing SWIFT-related systems and components” (e.g., servers, HSMs) within the user’s premises to prevent unauthorized access, tampering, or theft.
Select the environment that is not in scope in a SWIFT user CSP assessment (assuming the environments are separated).
•Swift Customer Security Controls Policy
•Swift Customer Security Controls Framework v2025
•Independent Assessment Framework
•Independent Assessment Process for Assessors Guidelines
•Independent Assessment Framework - High-Level Test Plan Guidelines
•Outsourcing Agents - Security Requirements Baseline v2025
•CSP Architecture Type - Decision tree
•CSP_controls_matrix_and_high_test_plan_2025
•Assessment template for Mandatory controls
•Assessment template for Advisory controls
•CSCF Assessment Completion Letter
•Swift_CSP_Assessment_Report_Template
SWIFT infrastructure (sometimes known as Live)
Development
Disaster Recovery
Cold backup systems
The CSCF defines the scope of environments for a SWIFT user CSP assessment, focusing on environments that handle live SWIFT transactions or are critical to operational continuity. The "Swift Customer Security Controls Framework v2025" and "Independent Assessment Framework" provide guidance on scope. Let’s evaluate each option, assuming the environments are separated:
•Option A: SWIFT infrastructure (sometimes known as Live)
This is in scope. The live environment, where actual SWIFT transactions are processed (e.g., Alliance Access sending MT103 messages), is the primary focus of the CSCF. Controls like "1.1 SWIFTEnvironment Protection" and "2.1 Internal Data Transmission Security" apply directly to this environment.
•Option B: Development
This is not in scope. Development environments, used for building or testing applications before deployment, are typically out of scope if they are fully separated from live systems and do not process real SWIFT data. The "Independent Assessment Framework" excludes development environments unless they are integrated with live systems, which the question assumes is not the case.
•Option C: Disaster Recovery
This is in scope. Disaster Recovery (DR) environments are designed to take over in case of a failure in the live environment. Since they can process live SWIFT transactions during a failover, they must comply with CSCF controls (e.g., Control "1.1") to ensure continuity and security.
•Option D: Cold backup systems
This is in scope. Cold backup systems, while not actively processing transactions, are part of the SWIFT infrastructure’s resilience strategy. They must be secured to prevent compromise (e.g., CSCF Control "1.2 Physical Security") and are included in the assessment scope per the "Assessment template for Mandatory controls."
Summary of Correct Answer:
The Development environment (B) is not in scope for a SWIFT user CSP assessment if separated from live systems.
References to SWIFT Customer Security Programme Documents:
•Swift Customer Security Controls Framework v2025: Excludes development environments from scope if separated.
•Independent Assessment Framework: Focuses on live, DR, and backup environments.
•Assessment template for Mandatory controls: Includes DR and backup systems in scope.
========
The SwiftNet Link (SNL) software is always required for the Swift Alliance Gateway to operate.
SIL Connectivity
•Generic
•Products Cloud
•Products OnPrem
•Security
TRUE
FALSE
SwiftNet Link (SNL) is a critical component of the SWIFT infrastructure, serving as the mandatory network interface for accessing SWIFTNet services. The Swift Alliance Gateway (SAG) is a communication interface that consolidates message flows from various applications and connects them to the SWIFT network. According to SWIFT documentation, SAG is a modular software package installed on top of SNL, meaning SNL is a foundational requirement for SAG to operate.
SNL provides essential functionalities such as transport, formatting, security, and service management, enabling secure and interoperable communication over the SWIFT Secure IP Network (SIPN). SAG uses SNL to establish this connectivity, as it does not have direct network access capabilities on its own. For example, SAG relies on SNL to handle SWIFT message types like FIN, InterAct, and FileAct, ensuring secure communication with the SWIFT network. This dependency is evident in architectures where SAG is deployed, such as in the Alliance Connect Virtual solutions, where SNL is always included alongside SAG to facilitate connectivity.
The mention of "SIL Connectivity" in the question refers to the SWIFT Integration Layer (SIL), which is often part of cloud-based deployments like Alliance Cloud. However, even in such setups, SNL remains a requirement for SAG to function, as SIL itself interacts with SAG/SNL to manage message flows. The categories "Generic," "Products Cloud," "Products OnPrem," and "Security" likely refer to the context of SWIFT services, but they do not alter the fundamental requirement of SNL for SAG operation.
There are no exceptions in SWIFT’s official documentation where SAG can operate without SNL. Even in cloud-based solutions like Alliance Cloud or Alliance Lite2, SNL is either embedded or provided as part of the connectivity stack. For instance, in Alliance Connect Virtual deployments, SAG and SNL are deployed together to ensure connectivity to SWIFTNet. Therefore, the statement is unequivocally true.
References to SWIFT Customer Security Programme Documents:
•SWIFT Customer Security Controls Framework (CSCF) v2024: The CSCF mandates secure connectivity components like SNL within the SWIFT secure zone (Control 1.1 SWIFT Environment Protection).
•SWIFT Alliance Gateway Documentation: SAG is described as requiring SNL for connectivity to SWIFTNet, as it acts as an interface on top of SNL.
•SWIFTNet Link Documentation: SNL is the mandatory network interface for all external SWIFTNet communications, including those facilitated by SAG.
The Internal Audit and an external assessment company are both involved in a SWIFT user’s assessment. Both have shared control assessments to cover the full scope (meaning two separate assessment teams). Who needs to provide a completion letter? (Select the correct answer)
•Swift Customer Security Controls Policy
•Swift Customer Security Controls Framework v2025
•Independent Assessment Framework
•Independent Assessment Process for Assessors Guidelines
•Independent Assessment Framework - High-Level Test Plan Guidelines
•Outsourcing Agents - Security Requirements Baseline v2025
•CSP Architecture Type - Decision tree
•CSP_controls_matrix_and_high_test_plan_2025
•Assessment template for Mandatory controls
•Assessment template for Advisory controls
•CSCF Assessment Completion Letter
•Swift_CSP_Assessment_Report_Template
The Internal audit lead assessor and the external company lead assessor
The Internal audit lead assessor only
The External company lead assessor only
None of them, it is not required when an internal department was involved in the assessment
The "Independent Assessment Framework" and "Independent Assessment Process for Assessors Guidelines" require that the CSP assessment be conducted by an independent, certified assessor, with the resulting "CSCF Assessment Completion Letter" being a key deliverable. Let’s evaluate each option:
•Option A: The Internal audit lead assessor and the external company lead assessor
This is incorrect. The CSP prohibits reliance on internal audits for the completion letter due to the independence requirement. Only the external assessor’s letter is valid, as per the "Independent Assessment Framework."
•Option B: The Internal audit lead assessor only
This is incorrect. Internal audits lack the independence needed to issue the completion letter, which must come from an external assessor.
•Option C: The External company lead assessor only
This is correct. The "Independent Assessment Process for Assessors Guidelines" mandates that the completion letter be provided by the lead assessor from the external assessment company, as they are the independent entity conducting the assessment. The internal audit’s involvement is supplementary and cannot replace the external assessor’s responsibility.
•Option D: None of them, it is not required when an internal department was involved in the assessment
This is incorrect. A completion letter is always required, and internal involvement does not waive this requirement; it must be issued by the external assessor.
Summary of Correct Answer:
Only the external company lead assessor needs to provide the completion letter (C).
References to SWIFT Customer Security Programme Documents:
•Independent Assessment Framework: Requires an independent assessor’s completion letter.
•Independent Assessment Process for Assessors Guidelines: Specifies external assessor responsibility.
•CSCF Assessment Completion Letter: Issued by the external assessor.
========
Which user roles are available in Alliance Cloud by default. (Choose all that apply.)

Role and Operator management
Message Management
Administrator
Message Security Administrator
This question pertains to the default user roles available in Alliance Cloud, a SWIFT cloud-based messaging solution:
Step 1: Alliance Cloud Overview
Alliance Cloud provides a hosted messaging service (e.g., for Alliance Lite2 or RMA), with predefined roles for managing operations, security, and messages. Default roles are outlined in the product documentation.
Select the correct statement(s) about the Swift Alliance Gateway. (Choose all that apply.)

It acts as the single window to SwiftNet messaging services byconcentratingyour traffic flows
It allows sharing of PKI profiles between application or individuals, through the use of virtual profiles
It allows the creation and/or modification of some Swift messages (depending on the types &/or formats)
The Alliance Gateway can only be accessed by a SWIFTNet user
The Swift Alliance Gateway is a critical component in the Swift ecosystem, designed to facilitate secure messaging and connectivity. Let’s evaluate each option based on theSwift Customer Security Controls Framework (CSCF) v2024and related documentation.
Step 1: Understand the Role of Swift Alliance Gateway
The Swift Alliance Gateway (SAG) is a software component that serves as a centralized entry point for SwiftNet messaging services. It handles traffic concentration, security, and connectivity management. This is detailed in theSwift Alliance Gateway User Guideand referenced in theCSCF v2024underControl 1.1: Swift Environment Protection.
Step 2: Evaluate Each Option
A. It acts as the single window to SwiftNet messaging services by concentrating your traffic flowsThe SAG is designed to consolidate and manage all SwiftNet traffic from a user’s environment,acting as a single point of access to SwiftNet services. This is a primary function, as confirmed in theSwift Alliance Gateway Technical Documentationand aligns withControl 1.1, which emphasizes secure traffic management.Conclusion: This statement is correct.
B. It allows sharing of PKI profiles between application or individuals, through the use of virtual profilesThe SAG supports the use of virtual PKI profiles to enable secure sharing of cryptographic identities across applications or users within the Swift environment. This feature enhances flexibility while maintaining security, as noted in theSwift Security Best PracticesandControl 2.5B: Cryptographic Key Management.Conclusion: This statement is correct.
C. It allows the creation and/or modification of some Swift messages (depending on the types &/or formats)The SAG is a gateway for message routing and security, not a tool for creating or modifying Swift messages. Message creation and modification are handled by applications like Alliance Access or Entry, not the Gateway. This is clarified in theSwift Alliance Gateway User Guide, which specifies its role as a connectivity and security layer.Conclusion: This statement is incorrect.
D. The Alliance Gateway can only be accessed by a SWIFTNet userThe SAG is accessed by authorized systems and users within the Swift user’s environment, not exclusively by SwiftNet users. It interfaces with operator systems, middleware, and other components, as perControl 1.2: Logical Access Control, which allows controlled access by authorized entities, not just SwiftNet users.Conclusion: This statement is incorrect.
Step 3: Conclusion and Verification
The verified statements areAandB, as they accurately reflect the SAG’s role in traffic concentration and PKI profile management, consistent with Swift CSP documentation.
References
Swift Alliance Gateway User Guide, Section: Functionality Overview.
Swift Customer Security Controls Framework (CSCF) v2024, Control 1.1: Swift Environment Protection, Control 2.5B: Cryptographic Key Management.
Swift Security Best Practices, Section: Alliance Gateway Configuration.
An application only uses (i) the SWIFT API for reporting and gpi basic tracker calls through (ii) a tailored account not allowing business transactions management. Is this application in scope of the CSCF? (Select the correct answer)
•Swift Customer Security Controls Policy
•Swift Customer Security Controls Framework v2025
•Independent Assessment Framework
•Independent Assessment Process for Assessors Guidelines
•Independent Assessment Framework - High-Level Test Plan Guidelines
•Outsourcing Agents - Security Requirements Baseline v2025
•CSP Architecture Type - Decision tree
•CSP_controls_matrix_and_high_test_plan_2025
•Assessment template for Mandatory controls
•Assessment template for Advisory controls
•CSCF Assessment Completion Letter
•Swift_CSP_Assessment_Report_Template
Yes, it is in scope and considered a customer connector because it reads business transaction data
No, it can be descoped because there is no business transaction management being performed
No, it is not in scope because the API connection method is not in scope of the CSP
Yes, it is in scope because the API connection method is less secure than SWIFT interfaces
The CSCF applies to all SWIFT users and components that handle SWIFT-related data or connectivity, including customer connectors and interfaces. The scope is defined by the "Swift Customer Security Controls Framework v2025" and the "CSP Architecture Type - Decision tree." Let’s evaluate the scenario and options:
•The application uses the SWIFT API for reporting and gpi basic tracker calls (e.g., tracking payment statuses via the SWIFT gpi Tracker) through a tailored account that does not allow business transaction management (e.g., creating or sending MT messages like MT103). This limits its functionality to read-only or monitoring activities.
•CSCF Scope: The CSCF applies to components that process or manage SWIFT business transactions (e.g., payment messages) or provide connectivity to the SWIFT network. The "CSP Architecture Type - Decision tree" classifies components into architecture types (A1-A4), with customer connectors and interfaces in scope if they handle transactional data or enable SWIFT connectivity. Reporting and tracking via APIs, without transaction management, do not constitute business transaction processing.
•Option A: Yes, it is in scope and considered a customer connector because it reads business transaction data
This is incorrect. While the application reads transaction data (e.g., via gpi Tracker), the CSCF scope is primarily focused on components that manage or transmit business transactions (e.g., creating or sending messages). Reading data for reporting purposes does not classify it as a customer connector requiring full CSCF compliance unless it also handles transactional flows. The "Swift_CSP_Assessment_Report_Template" focuses on transactional interfaces.
•Option B: No, it can be descoped because there is no business transaction management being performed
This is correct. Since the application does not manage business transactions (e.g., it cannot initiate or modify payments), it falls outside the primary scope of the CSCF. The "Independent Assessment Framework" allows for descoping of components that do not process transactional data, provided they are isolated from the SWIFT secure zone. This aligns with the "CSP Architecture Type - Decision tree," which excludes non-transactional reporting tools from mandatory assessment.
•Option C: No, it is not in scope because the API connection method is not in scope of the CSP
This is incorrect. The SWIFT API connection method is within the CSP scope if it interacts with SWIFT services (e.g., gpi Tracker), but the key factor is the lack of transaction management, not the API itself.
•Option D: Yes, it is in scope because the API connection method is less secure than SWIFT interfaces
This is incorrect. Security of the connection method (e.g., API vs. traditional interfaces) does not determine CSCF scope. The scope is based on functionality (transaction management), and the statement’s premise about security is not a valid criterion per CSCF guidelines.
Summary of Correct Answer:
The application is not in scope of the CSCF and can be descoped because it does not perform business transaction management (B).
References to SWIFT Customer Security Programme Documents:
•Swift Customer Security Controls Framework v2025: Defines scope based on transaction management.
•CSP Architecture Type - Decision tree: Guides descoping of non-transactional components.
•Independent Assessment Framework: Allows descoping of reporting-only applications.
========
Which statements are correct about the Alliance Access LSO and RSO? (Select the two correct answers that apply)
•Connectivity
•Generic
•Products Cloud
•Products OnPrem
•Security
They are Alliance Security Officers
Their PKI certificates are stored either on an HSM Token or on an HSM-box
They are the business profiles that can sign the SWIFT financial transactions
They are responsible for the configuration and management of the security functions in the messaging interface
The Local Security Officer (LSO) and Remote Security Officer (RSO) are roles defined within the SWIFT Alliance suite, particularly for managing security in messaging interfaces like Alliance Access. Let’s evaluate each option:
•Option A: They are Alliance Security Officers
This is correct. The LSO and RSO are collectively referred to as Alliance Security Officers within the SWIFT ecosystem. The LSO is typically an on-site officer responsible for local security management, while the RSO can perform similar functions remotely, often for distributed environments. These roles are critical for configuring and maintaining security settings in Alliance Access, as outlined in SWIFT’s operational documentation. The CSCF Control "6.1 Security Awareness" emphasizes the importance of trained security officers, which aligns with the LSO/RSO roles.
•Option B: Their PKI certificates are stored either on an HSM Token or on an HSM-box
This is incorrect. While PKI certificates are used for authentication and are managed within the SWIFT environment, they are not specifically tied to the LSO or RSO roles in terms of storage. PKI certificates for SWIFTNet are stored and managed by the Hardware Security Module (HSM), either as an HSM token (e.g., a smart card) or an HSM-box (e.g., a physical or virtual HSM device). However, these certificates are associated with the SWIFT application or user roles (e.g., for message signing), not the LSO/RSO profiles themselves. The LSO/RSO uses these certificates as part of their duties, but the statement implies ownership or storage, which is inaccurate. CSCF Control "1.3 Cryptographic Failover" specifies HSM management, not LSO/RSO certificate storage.
•Option C: They are the business profiles that can sign the SWIFT financial transactions
This is incorrect. The LSO and RSO are security management roles, not business profiles authorized to sign financial transactions. Signing SWIFT financial transactions (e.g., MT103 messages) is the responsibility of authorized business users or automated processes within Alliance Access, who use PKI certificates managed by the HSM. The LSO/RSO’s role is to configure and oversee security, not to perform transactional activities. This distinction is clear in SWIFT’s role-based access control documentation.
•Option D: They are responsible for the configuration and management of the security functions in the messaging interface
This is correct. The LSO and RSO are tasked with configuring and managing security functions within Alliance Access, such as user access control, authentication settings, and compliance with CSCF requirements. This includes managing PKI certificate usage, setting up secure communication channels, and ensuring the messaging interface adheres to security policies. For example, the LSO can define security profiles and monitor access, as detailed in the Alliance Access Administration Guide, aligning with CSCF Control "2.1 Internal Data Transmission Security."
Summary of Correct Answers:
The LSO and RSO are Alliance Security Officers (A) and are responsible for the configuration and management of security functions in the messaging interface (D). Their PKI certificates are not stored by them, and they do not sign transactions.
References to SWIFT Customer Security Programme Documents:
•SWIFT Customer Security Controls Framework (CSCF) v2024: Control 6.1 highlights the role of security officers like LSO/RSO.
•SWIFT Alliance Access Documentation: Describes LSO/RSO responsibilities for security configuration.
•SWIFT Security Guidelines: Details PKI certificate management by HSM, not LSO/RSO.
========
Which of the following statements best describes the difference between an audit and an assessment as per SWIFT CSP definitions? (Select the correct answer)
•Swift Customer Security Controls Policy
•Swift Customer Security Controls Framework v2025
•Independent Assessment Framework
•Independent Assessment Process for Assessors Guidelines
•Independent Assessment Framework - High-Level Test Plan Guidelines
•Outsourcing Agents - Security Requirements Baseline v2025
•CSP Architecture Type - Decision tree
•CSP_controls_matrix_and_high_test_plan_2025
•Assessment template for Mandatory controls
•Assessment template for Advisory controls
•CSCF Assessment Completion Letter
•Swift_CSP_Assessment_Report_Template
An audit is a comprehensive review of a customer’s controls to ensure they meet regulatory requirements, while an assessment is a very high-level review of controls to identify potential weaknesses
An audit looks at the defined controls design and implementation compliance and follows recognized international audit standards, whereas an assessment is less strict but aims the same common objectives
An audit is a one-time event, while an assessment is an ongoing process of monitoring and improving security controls
An audit and an assessment can be used interchangeably
The "Independent Assessment Framework" and "Independent Assessment Process for Assessors Guidelines" distinguish between audits and assessments within the SWIFT CSP context. Let’s evaluate each option:
•Option A: An audit is a comprehensive review of a customer’s controls to ensure they meet regulatory requirements, while an assessment is a very high-level review of controls to identify potential weaknesses
This is incorrect. The CSP assessment is a detailed, independent evaluation of CSCF compliance, not a high-level review. Audits may focus on broader regulatory compliance, but the CSP assessment is specific to CSCF controls.
•Option B: An audit looks at the defined controls design and implementation compliance and follows recognized international audit standards, whereas an assessment is less strict but aims the same common objectives
This is correct. The CSP defines an assessment as a structured, independent process to verify CSCF control compliance, guided by SWIFT-specific guidelines rather than international audit standards (e.g., ISAE 3000). Audits, while thorough, follow broader standards and may not align with CSP’s tailored objectives. The "Independent Assessment Process for Assessors Guidelines" supports this distinction, noting assessments are CSP-specific with a focus on effectiveness.
•Option C: An audit is a one-time event, while an assessment is an ongoing process of monitoring and improving security controls
This is incorrect. Both audits and assessments can be one-time or periodic. The CSP assessment is an annual requirement, not an ongoing process, per the "Independent Assessment Framework."
•Option D: An audit and an assessment can be used interchangeably
This is incorrect. The CSP clearly differentiates between the two, with assessments being the mandated method for CSCF compliance.
Summary of Correct Answer:
An audit follows international standards for control compliance, while an assessment is CSP-specific with similar objectives but less strict standards (B).
References to SWIFT Customer Security Programme Documents:
•Independent Assessment Process for Assessors Guidelines: Defines assessment scope.
•Independent Assessment Framework: Distinguishes assessment from audit.
•Swift_CSP_Assessment_Report_Template: Outlines assessment process.
========
From the outsourcing agent diagram, which components in the diagram are in scope and applicable for the Swift user.

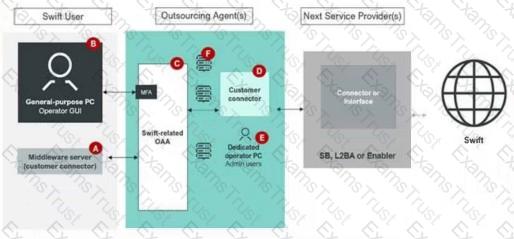
Components A, B, C, D and E
Components A and B
Components C, D and E
None of the above
This question determines which components in the outsourcing agent diagram are in scope and applicable for the Swift user under theSwift Customer Security Controls Framework (CSCF) v2024.
Step 1: Understand CSCF Scope and the Diagram
TheCSCF v2024defines the scope as systems directly involved in Swift messaging, connectivity, or security within the user’s control or responsibility, including those managed by outsourcing agents. The diagram includes:
A. Middleware server (customer connector): Part of the Swift user’s environment.
B. General-purpose PC Operator GUI: An operator system in the user’s environment.
C. Swift-related OAA: The messaging interface in the outsourcing agent’s environment.
D. Customer connector: A connector in the outsourcing agent’s environment interfacing with the next service provider.
E. Dedicated PC Admin users: Administrative systems in the outsourcing agent’s environment.
TheIndependent Assessment Frameworkholds the Swift user accountable for in-scope components, even when outsourced, perControl 1.1: Swift Environment Protection.
Step 2: Analyze Component Applicability
A. Middleware server (customer connector): Located in the Swift user’s environment, this connects to the outsourcing agent. While it facilitates Swift traffic, it is typically considered part of the user’s local infrastructure and not directly in the outsourcing agent’s scope for user responsibility, unless explicitly outsourced. TheCSCF v2024scope focuses on Swift-related systems managed by the outsourcing agent when the user relies on them.
B. General-purpose PC Operator GUI: This is a user-side operator system, not a core Swift component. PerControl 1.2: Logical Access Control, it is out of the secure zone and not in scope for the outsourcing agent’s responsibility.
C. Swift-related OAA: This is the messaging interface (e.g., Alliance Access) managed by the outsourcing agent. It is in scope for the Swift user, as they are responsible for its security and compliance, perControl 1.1.
D. Customer connector: This connector, within the outsourcing agent’s environment, interfaces with the next service provider (e.g., SB, L2BA). It is in scope, as the user must ensure its security underControl 1.1.
E. Dedicated PC Admin users: These administrative systems, managed by the outsourcing agent, are in scope because they control Swift-related components, perControl 1.2.
Step 3: Match with Options
A. Components A, B, C, D and E: Includes A and B, which are not in scope for the outsourcing agent’s responsibility under the user’s purview.
B. Components A and B: Only includes user-side components, not the outsourcing agent’s in-scope systems.
C. Components C, D and E: Includes the outsourcing agent’s Swift-related OAA, customer connector, and admin PCs, which are in scope for the user’s compliance responsibility.
D. None of the above: Incorrect, as C, D, and E are applicable.
Step 4: Conclusion and Verification
The correct answer isC, as Components C, D, and E, managed by the outsourcing agent, are in scope and applicable for the Swift user’s compliance under theCSCF v2024.
References
Swift Customer Security Controls Framework (CSCF) v2024, Control 1.1: Swift Environment Protection, Control 1.2: Logical Access Control.
Swift Independent Assessment Framework, Section: Outsourcing Scope.
Swift Outsourcing Guidelines, Section: User Responsibility.
Must Swift users submit a copy of their final assessment report to Swift?

Yes, all documents produced from the assessment must be provided proactively to Swift
No, it is not required to provide Swift with any documents by default. However, Swift can request a copy of the Assessment completion letter
Yes, a copy of (only) the assessment report must be provided to Swift, no other documents
Yes, in cases where a customer performs an Independent assessment rather than an audit then a copy of the assessment report must be provided. However, it is not required for the Swift user to provide any forms when an Internal/External Audit is performed
This question addresses the obligations of Swift users regarding the submission of assessment-related documents to Swift under the Customer Security Programme (CSP).
Step 1: Understand CSP Assessment Submission Requirements
TheSwift Customer Security Controls Framework (CSCF) v2024and theIndependent Assessment Frameworkoutline the process for CSP assessments, including what must be submitted to Swift. The focus is on ensuring compliance through attestation, with specific deliverables defined.
Step 2: Evaluate Each Option
A. Yes, all documents produced from the assessment must be provided proactively to SwiftThis is incorrect. TheIndependent Assessment Frameworkdoes not require proactive submission of all assessment documents (e.g., detailed reports, working papers). Only the completion letter and attestation are typically submitted unless otherwise requested by Swift.Conclusion: Incorrect.
B. No, it is not required to provide Swift with any documents by default. However, Swift can request a copy of the Assessment completion letterTheCSCF v2024andIndependent Assessment Frameworkstate that users are not required to proactively submit the full assessment report or other documents. However, Swift retains the right to request the completion letter (certifying assessment completion) or additional evidence during quality assurance reviews. This aligns with theSwift CSP Compliance Guidelines.Conclusion: Correct.
C. Yes, a copy of (only) the assessment report must be provided to Swift, no other documentsThis is incorrect. The full assessment report is not mandated for proactive submission; only the completion letter is typically required unless requested. TheIndependent Assessment Frameworkemphasizes the completion letter as the key deliverable.Conclusion: Incorrect.
D. Yes, in cases where a customer performs an Independent assessment rather than an audit then a copy of the assessment report must be provided. However, it is not required for the Swift user to provide any forms when an Internal/External Audit is performedThis is partially misleading. TheIndependent Assessment Frameworkdoes not distinguish between independent assessments and audits in terms of mandatory report submission. For both, the completion letter is the default submission, with reports requested only if needed. The differentiation based on assessment type is not supported byCSCF v2024guidelines.Conclusion: Incorrect.
Step 3: Conclusion and Verification
The correct answer isB, as theCSCF v2024andIndependent Assessment Frameworkdo not require proactive submission of the full assessment report, but Swift can request the completion letter as part of its oversight process.
References
Swift Customer Security Controls Framework (CSCF) v2024, Section: Independent Assessment Requirements.
Swift Independent Assessment Framework, Section: Deliverables and Submission.
Swift CSP Compliance Guidelines, Section: Document Submission Rules.
Who can connect to SWIFT? (Select all answers that apply)
•Connectivity
•Generic
•Products Cloud
•Products OnPrem
•Security
Financial institutions, such as banks and securities broker-dealers
Individuals who use online banking for international transfers
Market infrastructures that provide financial institutions with centralized transaction processing
Corporates that work with multiple banking partners
SWIFT (Society for Worldwide Interbank Financial Telecommunication) is a global cooperative that provides a secure messaging network primarily for financial transactions. Its services are designed for entities involved in the financial ecosystem, and access is restricted to members or participants who meet SWIFT’s membership criteria. Let’s evaluate each option:
•Option A: Financial institutions, such as banks and securities broker-dealers
This is correct. SWIFT’s core users are financial institutions, including banks, broker-dealers, and other entities regulated under financial authorities. These institutions are direct members of SWIFT or connect through correspondent banking relationships. The SWIFT Customer Security Programme (CSP) and CSCF are tailored to secure the messaging environment for these entities, with controls like "1.1 SWIFT Environment Protection" designed to safeguard their operations. Membership requires adherence to SWIFT’s security standards, and these institutions use SWIFTNet for payments, securities, trade, and treasury services.
•Option B: Individuals who use online banking for international transfers
This is incorrect. Individuals, including those using online banking for international transfers, do not connect directly to SWIFT. Instead, they rely on their banks or financial service providers, which act as intermediaries using SWIFT’s network. SWIFT is a business-to-business (B2B) network, not a consumer-facing platform. The CSCF does not address individual users; its focus is on institutional security controls, such as those protecting the SWIFT secure zone.
•Option C: Market infrastructures that provide financial institutions with centralized transaction processing
This is correct. Market infrastructures, such as clearinghouses, central securities depositories (CSDs), and payment systems (e.g., TARGET2 or CHAPS), are eligible to connect to SWIFT. These entities facilitate centralized transaction processing for financial institutions and are part of the broader financial ecosystem. SWIFT documentation recognizes their role, and they are subject to the same security requirements under the CSP. For example, CSCF Control "1.2 Physical Security" applies to these infrastructures when they host SWIFT-related components.
•Option D: Corporates that work with multiple banking partners
This is correct. Corporates, especially large multinational corporations with complex financial operations, can connect to SWIFT through SWIFT’s corporate connectivity options, such as Alliance Lite2 or SWIFT for Corporates. These services allow corporates to send and receive payment instructions directly via SWIFTNet, bypassing some intermediary steps with banks. This capability is outlined in SWIFT’s corporate access documentation, and such entities must comply with CSP security controls when integrating with the SWIFT network. The CSCF extends to these participants, ensuring their environments are secure (e.g., Control "6.1 Security Awareness").
Summary of Correct Answers:
Financial institutions (A), market infrastructures (C), and corporates with multiple banking partners (D) can connect to SWIFT, either as direct members or through specific connectivity options. Individuals (B) do not have direct access.
References to SWIFT Customer Security Programme Documents:
•SWIFT Customer Security Controls Framework (CSCF) v2024: Applies to all SWIFT users, including financial institutions, market infrastructures, and corporates, with security controls tailored to their environments (Controls 1.1, 6.1).
•SWIFT Membership Guidelines: Outlines eligibility for financial institutions, market infrastructures, and corporates, excluding individuals.
•SWIFT for Corporates Documentation: Details corporate connectivity options like Alliance Lite2.
May an assessor rely on an ISAE 3000 report dating back 2 years to support a CSP independent assessment? (Select the correct answer)
•Swift Customer Security Controls Policy
•Swift Customer Security Controls Framework v2025
•Independent Assessment Framework
•Independent Assessment Process for Assessors Guidelines
•Independent Assessment Framework - High-Level Test Plan Guidelines
•Outsourcing Agents - Security Requirements Baseline v2025
•CSP Architecture Type - Decision tree
•CSP_controls_matrix_and_high_test_plan_2025
•Assessment template for Mandatory controls
•Assessment template for Advisory controls
•CSCF Assessment Completion Letter
•Swift_CSP_Assessment_Report_Template
No, that is too old, the maximum is 18 months
Yes, there is no time limit for an ISAE 3000 report
No, an ISAE 3000 report is no valid substitute as a rule
Yes, provided there is no change to the SWIFT user’s infrastructure
The "Independent Assessment Process for Assessors Guidelines" and "Independent Assessment Framework" provide guidance on using external audit reports (e.g., ISAE 3000) to support CSP assessments. ISAE 3000 is an international standard for assurance engagements. Let’s evaluate each option:
•Option A: No, that is too old, the maximum is 18 months
This is correct. The CSP specifies that external reports like ISAE 3000 must be no older than 18 months to ensure relevance, as security environments can change. The "Independent Assessment Framework" and "CSP_controls_matrix_and_high_test_plan_2025" set this time limit to validate current compliance status.
•Option B: Yes, there is no time limit for an ISAE 3000 report
This is incorrect. A time limit is enforced to ensure the report reflects the current security posture, as per CSP guidelines.
•Option C: No, an ISAE 3000 report is no valid substitute as a rule
This is incorrect. An ISAE 3000 report can be used as supporting evidence if relevant and recent, but it is not a full substitute for the independent assessment, per the "Independent Assessment Process for Assessors Guidelines."
•Option D: Yes, provided there is no change to the SWIFT user’s infrastructure
This is incorrect. Even with no changes, the 18-month limit applies to ensure the report’s currency, not just infrastructure stability.
Summary of Correct Answer:
An assessor cannot rely on an ISAE 3000 report dating back 2 years; the maximum is 18 months (A).
References to SWIFT Customer Security Programme Documents:
•Independent Assessment Process for Assessors Guidelines: Limits ISAE 3000 reports to 18 months.
•Independent Assessment Framework: Specifies timeframe for external evidence.
•CSP_controls_matrix_and_high_test_plan_2025: Enforces currency of supporting reports.
========
Where is the implementation of multi-factor authentication deemed sufficient to support control 4.2 compliance? (Choose all that apply.)

When accessing an outsourcing agent or an L2BA Swift-related application
When logging-in on an interface, a connector, or the system running such component
When login on the jump server filtering access to local Swift secure zone
On the General Operator PC used to access a Swift-related component
Control 4.2 of the Swift Customer Security Controls Framework (CSCF) mandates the implementation of Multi-Factor Authentication (MFA) to "prevent compromise of a single authentication factor allowing access to SWIFT systems." The control applies to various access points within the SWIFT environment to ensure robust security. Let’s evaluate each option against CSCF v2024 and related guidelines:
A. When accessing an outsourcing agent or an L2BA Swift-related application
CSCF v2024 Control 4.2 explicitly states that MFA is required for "SWIFT-related applications or components managed by third-party service providers" (e.g., outsourcing agents) and Level 2 Business Applications (L2BA). This ensures that external entitieshandling SWIFT-related processes adhere to the same security standards. The scope includes any operator access to these applications, making MFA mandatory here.
In a fully on-premises infrastructure, which security management profile is not involved? (Select the one correct answer)
•Connectivity
•Generic
•Products Cloud
•Products OnPrem
•Security
Alliance Security Officer (LSO/RSO)
HSM Administrator
swift.com Administrator
Customer Security Officer
In a fully on-premises infrastructure, all SWIFT-related components (e.g., Alliance Gateway, SwiftNet Link, HSM) are hosted and managed locally by the customer. This setup contrasts with cloud-based deployments (e.g., Alliance Cloud), where some management is outsourced to SWIFT or third-party providers. The security management profiles refer to roles responsible for overseeing the security of the SWIFT environment. Let’s evaluate each option:
•Option A: Alliance Security Officer (LSO/RSO)
This is involved. The Local Security Officer (LSO) and Remote Security Officer (RSO) are roles defined by SWIFT for managing security settings within the Alliance suite (e.g., Alliance Gateway, Alliance Access). In an on-premises setup, the LSO/RSO is typically an internal staff member who configures security parameters, manages user access, and ensures compliance with CSCF controls like "6.1 Security Awareness." These roles are mandatory for on-premises deployments.
•Option B: HSM Administrator
This is involved. The HSM Administrator is responsible for managing the Hardware Security Module, which stores PKI certificates and performs cryptographic operations. In an on-premises environment, the customer maintains the HSM locally, and the HSM Administrator oversees its configuration and security, aligning with CSCF Control "1.3 Cryptographic Failover." This role is essential for on-premises security management.
•Option C: swift.com Administrator
This is not involved. The "swift.com Administrator" is not a standard SWIFT-defined role. It appears to be a misnomer or typo, possibly intended to refer to a SWIFT-hosted service administrator (e.g., someone managing swift.com-related cloud services). In a fully on-premises infrastructure, there is no reliance on SWIFT-hosted services or cloud management, as all components are locally controlled. SWIFT’s cloud offerings (e.g., Alliance Cloud) involve administrators managing SWIFT-hosted infrastructure, but this is irrelevant in an on-premises context. The CSCF does not reference a "swift.com Administrator" role for on-premises setups.
•Option D: Customer Security Officer
This is involved. The Customer Security Officer is a role mandated by the SWIFT CSP, responsible for overseeing the institution’s compliance with the CSCF. In an on-premises environment, this officer ensures that local security controls (e.g., physical security under Control "1.2") are implemented and audited, making this role essential.
Summary of Correct Answer:
In a fully on-premises infrastructure, the "swift.com Administrator" (Option C) is not involved, as it does not apply to locally managed environments and is likely a reference to a cloud-based role.
References to SWIFT Customer Security Programme Documents:
•SWIFT Customer Security Controls Framework (CSCF) v2024: Defines roles like LSO/RSO, HSM Administrator, and Customer Security Officer for on-premises security (Controls 1.1, 1.3, 6.1).
•SWIFT Alliance Documentation: Describes the LSO/RSO and HSM Administrator roles in on-premises deployments.
•SWIFT CSP Compliance Guidelines: Mandates the Customer Security Officer role for all SWIFT users, including on-premises setups.
========
Additional Notes
•Typing Corrections: Corrected "ijp" to "P" for consistency in category labels. Adjusted "c" to "C" and "0" to "D" in question options for proper formatting.
•Context of Categories: The categories ("Connectivity," "Generic," "Products Cloud," "Products OnPrem," "Security") likely indicate the scope of the certification test, with "Products OnPrem" being relevant to Questions 4 and 5.
•SWIFT CSP Alignment: Answers align with the CSP’s focus on security roles and infrastructure types, as documented in the CSCF and SWIFT operational guides.
The SwiftNet Link (SNL) software is always required for the Swift Alliance Gateway to operate.
•Connectivity
•Generic
•Products Cloud
•Products OnPrem
•Security
TRUE
FALSE
SwiftNet Link (SNL) is the mandatory network interface software that enables connectivity to the SWIFTNet network, providing transport, security, and service management functionalities. The Swift Alliance Gateway (SAG) is a communication interface that consolidates message flows and relies on SNL to connect to SWIFTNet. According to SWIFT documentation, SAG is built on top of SNL, making SNL a prerequisite for SAG operation. This dependency is consistent across on-premises and cloud-based deployments (e.g., Alliance Connect Virtual), where SNL ensures secure communication over the SWIFT Secure IP Network (SIPN). The CSCF Control "1.1 SWIFT Environment Protection" underscores the need for secure connectivity components like SNL. There are no documented scenarios where SAG can operate without SNL, confirming the statement is true.
References to SWIFT Customer Security Programme Documents:
•SWIFT Customer Security Controls Framework (CSCF) v2024: Control 1.1 mandates secure connectivity components like SNL.
•SWIFT Alliance Gateway Documentation: SAG requires SNL for SWIFTNet connectivity.
•SWIFTNet Link Documentation: SNL is the mandatory interface for all SWIFTNet communications.
========
The cluster of VPN boxes is also called managed-customer premises equipment (M-CPE).

TRUE
FALSE
This question addresses the terminology related to VPN boxes in the Swift environment and their association with managed-customer premises equipment (M-CPE). Let’s verify this based on Swift CSP documentation.
Step 1: Understand VPN Boxes and M-CPE in Swift Context
In the Swift ecosystem, VPN boxes are typically part of the connectivity infrastructure used to establish secure tunnels (e.g., Network Transport Layer Security - NTLS) for communication with the Swift network. The term "managed-customer premises equipment (M-CPE)" generally refers to hardware or devices managed by a service provider or third party on the customer’s premises, often in telecommunications or IT contexts. TheSwift Customer Security Controls Framework (CSCF) v2024and related technical documentation provide insights into Swift’s infrastructure terminology.
Step 2: Analyze the Statement
The statement claims that the "cluster of VPN boxes is also called managed-customer premises equipment (M-CPE)." We need to determine if this is an official or recognized designation within the Swift CSP.
Step 3: Evaluate Against Swift CSP Guidelines
TheSwift Alliance Gateway Technical DocumentationandSwift Security Best Practicesdescribe VPN boxes (or similar connectivity devices) as part of the SwiftNet Link (SNL) infrastructure, often deployed at the user’s premises to secure communications. These devices are typically managed by the Swift user or a designated service provider, depending on the architecture (e.g., A2 or A4).
The term "M-CPE" is not specifically defined or used in Swift CSP documentation (e.g.,CSCF v2024,Swift User Handbook, orSwift Network Security Guidelines). Instead, Swift refers to such equipment as part of the "customer premises equipment (CPE)" when managed by the user, or as "managed services" when outsourced to a provider. However, "M-CPE" as a specific term for a cluster of VPN boxes is not corroborated.
In some IT contexts outside Swift, M-CPE might imply managed equipment, but Swift’s documentation does not adopt this terminology for VPN clusters, which are considered part of the broader connectivity infrastructure.
Step 4: Conclusion and Verification
The statement isFALSEbecause theCSCF v2024and related Swift documentation do not use "managed-customer premises equipment (M-CPE)" as a term for a cluster of VPN boxes. The correct terminology aligns with "customer premises equipment" or "managed connectivity devices," depending on the setup, but not specifically M-CPE.
References
Swift Customer Security Controls Framework (CSCF) v2024, Control 1.1: Swift Environment Protection.
Swift Alliance Gateway Technical Documentation, Section: Connectivity Infrastructure.
Swift Security Best Practices, Section: Network Security Devices.
In the illustration, identify the component type of each of the numbered components.

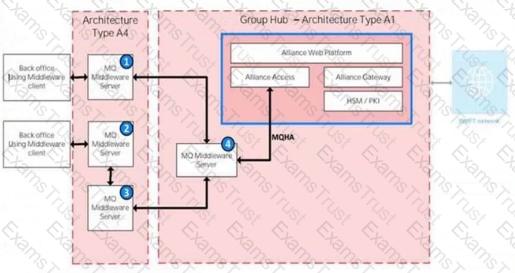
1. Customer Connector
2. Bridging Server (Middleware Server)
3. Customer Connector
4. Bridging Server (Middleware Server)
1. Customer Connector
2. Bridging Server (Middleware Server)
3. Customer Connector
4. Customer Connector
1. Bridging Server (Middleware Server)
2. Bridging Server (Middleware Server)
3. Bridging Server (Middleware Server)
4. Bridging Server (Middleware Server)
1. Customer Connector
2. Customer Connector
3. Customer Connector
4. Customer Connector
This question requires identifying the component types of the numbered components (1, 2, 3, and 4) in the provided diagram, which illustrates a Swift infrastructure with Architecture Type A4 (user environment) and Architecture Type A1 (group hub). The classification is based on theSwift Customer Security Controls Framework (CSCF) v2024and related architecture definitions.
Step 1: Understand the Diagram and Component Types
The diagram shows two environments:
Architecture Type A4: The user’s local environment with back-office systems using middleware clients and servers.
Architecture Type A1: A group hub hosting Swift components like Alliance Access, Alliance Gateway, and HSM/PKI, connecting to the Swift network.
Component Types:
Customer Connector: A system or server that facilitates connectivity between the user’s environment and the Swift infrastructure (e.g., middleware servers interfacing with the group hub).
Bridging Server (Middleware Server): A server that bridges data flows between back-office systems and the Swift messaging environment, often handling message queuing or transformation.
Step 2: Analyze Each Numbered Component
Component 1 (Middleware Server connected to Back Office 1):This server is part of the A4 architecture, interfacing the back-office middleware client with the group hub (A1). It acts as a connector, facilitating data exchange to the MQHA (Message Queue High Availability) server in the group hub. Per theCSCF v2024andSwift Architecture Types Explained, this is aCustomer Connector.
Component 2 (MQHA Middleware Server in the Group Hub):This server is within the A1 group hub, bridging the user’s data (via the customer connector) tothe Alliance Access and Gateway. It handles message queuing and acts as aBridging Server (Middleware Server), as defined in theSwift Alliance Gateway Technical Documentation.
Component 3 (Middleware Server connected to Back Office 2):Similar to Component 1, this server connects the second back-office middleware client to the MQHA server in the group hub, functioning as aCustomer Connector.
Component 4 (MQ Middleware Server connected to MQHA):This server within the A1 group hub supports the MQHA, bridging data flows to the Swift messaging components (Alliance Access/Gateway). It is aBridging Server (Middleware Server), consistent with theCSCF v2024definitions.
Step 3: Match with Options
A. 1. Customer Connector, 2. Bridging Server (Middleware Server), 3. Customer Connector, 4. Bridging Server (Middleware Server): Matches the analysis above.
B. 1. Customer Connector, 2. Bridging Server (Middleware Server), 3. Customer Connector, 4. Customer Connector: Incorrect, as Component 4 is a bridging server, not a customer connector.
C. 1. Bridging Server (Middleware Server), 2. Bridging Server (Middleware Server), 3. Bridging Server (Middleware Server), 4. Bridging Server (Middleware Server): Incorrect, as Components 1 and 3 are customer connectors, not bridging servers.
D. 1. Customer Connector, 2. Customer Connector, 3. Customer Connector, 4. Customer Connector: Incorrect, as Components 2 and 4 are bridging servers.
Step 4: Conclusion and Verification
The correct answer isA, as it accurately identifies the component types based on their roles in the A4 and A1 architectures, consistent withCSCF v2024andSwift Architecture Types Explained.
References
Swift Customer Security Controls Framework (CSCF) v2024, Control 1.1: Swift Environment Protection.
Swift Architecture Types Explained, Section: Component Roles.
Swift Alliance Gateway Technical Documentation, Section: Middleware and Connectors.
What type of control effectiveness needs to be validated for an independent assessment?

Effectiveness is never validated only the control design
An independent assessment is a point in time review with possible reviews of older evidence as appropriate
Operational effectiveness needs to be validated
None of the above
This question addresses the type of control effectiveness that must be validated during an independent assessment under the Swift Customer Security Programme (CSP). Let’s analyze this based on theSwift Customer Security Controls Framework (CSCF)and related guidelines.
Step 1: Understand Independent Assessments in Swift CSP
The Swift CSP mandates that users undergo an independent assessment to validate their compliance with the CSCF controls. This requirement is detailed in theCSCF v2024, under theIndependent Assessment Framework. The purpose of the assessment is to ensure that controls are not only designed appropriately but also implemented and operating effectively.
Step 2: Evaluate Each Option
A. Effectiveness is never validated only the control designThis statement is incorrect. TheIndependent Assessment Frameworkexplicitly requiresvalidation of both the design and theoperational effectivenessof controls. Assessing only the design without confirming that the control is working as intended does not meet Swift’s compliance requirements.Conclusion: This is incorrect.
B. An independent assessment is a point in time review with possible reviews of older evidence as appropriateWhile this statement is factually true (an independent assessment is indeed a point-in-time review, as per theCSCF v2024), it does not directly answer the question about what type of control effectiveness needs to be validated. It describes the nature of the assessment, not the focus of validation.Conclusion: This does not address the question directly.
C. Operational effectiveness needs to be validatedTheIndependent Assessment Frameworkspecifies that an independent assessment must validate both the design and the operational effectiveness of CSCF controls. Operational effectiveness ensures that controls are functioning as intended over a period of time, not just designed correctly on paper. This includes testing controls (e.g., logging, access controls) to confirm they are working in practice, as required for attestation.Conclusion: This is correct.
D. None of the aboveSince option C is correct, this option is not applicable.Conclusion: This is incorrect.
Step 3: Conclusion and Verification
The correct answer isC, as theCSCF v2024andIndependent Assessment Frameworkrequire validation of the operational effectiveness of controls during an independent assessment, ensuring that controls are not only designed but also implemented and functioning effectively.
References
Swift Customer Security Controls Framework (CSCF) v2024, Section: Independent Assessment Requirements.
Swift Independent Assessment Framework, Section: Assessment Scope and Objectives.
Swift CSP FAQ, Section: Independent Assessment Guidelines.
Is it mandated to perform security awareness and other specific trainings every year for individuals with SWIFT-critical roles? (Select the correct answer)
•Swift Customer Security Controls Policy
•Swift Customer Security Controls Framework v2025
•Independent Assessment Framework
•Independent Assessment Process for Assessors Guidelines
•Independent Assessment Framework - High-Level Test Plan Guidelines
•Outsourcing Agents - Security Requirements Baseline v2025
•CSP Architecture Type - Decision tree
•CSP_controls_matrix_and_high_test_plan_2025
•Assessment template for Mandatory controls
•Assessment template for Advisory controls
Yes, and a track record must show that both awareness and specific training are performed annually
No, both awareness and specific trainings are planned when deemed required
No, awareness training expected to be performed yearly; specific training to maintain the required knowledge only when needed
No, a track record must show that both awareness and specific training are performed at least bi-yearly (every 2 years)
CSCF Control "6.1 Security Awareness" mandates training for individuals with SWIFT-critical roles (e.g., LSO, RSO, operators) to ensure they understand security policies and procedures. Let’s evaluate each option:
•Option A: Yes, and a track record must show that both awareness and specific training are performed annually
This is correct. Control 6.1 requires annual security awareness training for all SWIFT-critical personnel, with additional specific training as needed to maintain knowledge. The "Swift Customer SecurityControls Framework v2025" and "Assessment template for Mandatory controls" mandate annual training and require a track record (e.g., logs or certificates) to demonstrate compliance.
•Option B: No, both awareness and specific trainings are planned when deemed required
This is incorrect. The CSCF mandates annual awareness training, not just ad-hoc planning, to ensure consistent security awareness.
•Option C: No, awareness training expected to be performed yearly; specific training to maintain the required knowledge only when needed
This is incorrect. While specific training can be as needed, awareness training is explicitly required annually, making this option partially inaccurate.
•Option D: No, a track record must show that both awareness and specific training are performed at least bi-yearly (every 2 years)
This is incorrect. The CSCF requires annual awareness training, not bi-yearly, as specified in the guidelines.
Summary of Correct Answer:
It is mandated to perform security awareness and specific trainings every year, with a track record (A).
References to SWIFT Customer Security Programme Documents:
•Swift Customer Security Controls Framework v2025: Control 6.1 mandates annual training.
•Assessment template for Mandatory controls: Requires annual training records.
•Independent Assessment Framework: Verifies training frequency.
========
Which encryption methods are used to secure the communications between the SNL host and HSM boxes?

NTLS and SSH
Telnet and SSL
NTLS and Telnet
MPLS and SSL
This question focuses on the encryption methods securing communications between the SwiftNet Link (SNL) host and Hardware Security Module (HSM) boxes in the Swift environment.
Step 1: Understand SNL and HSM Communication
The SwiftNet Link (SNL) facilitates secure connectivity to the Swift network, while the HSM manages cryptographic keys. Secure communication between the SNL host and HSM is critical, as outlined inControl 2.5B: Cryptographic Key Managementof theCSCF v2024. These communications must use strong encryption protocols.
Step 2: Evaluate Each Option
A. NTLS and SSH
NTLS (Network Transport Layer Security): This is Swift’s proprietary protocol for securing communications over the SwiftNet network, including between SNL and HSM. It provides end-to-end encryption and is widely used in Swift infrastructure, as confirmed in theSwift Alliance Gateway Technical Documentation.
SSH (Secure Shell): SSH is used for secure management and administration of HSMs and SNL hosts, enabling encrypted remote access and configuration, as noted inSwift Security Best Practices.This combination aligns with Swift’s security requirements for protecting HSM communications.Conclusion: This is correct.
B. Telnet and SSL
Telnet: An unencrypted protocol, unsuitable for secure communications, and not used in Swift’s security framework perControl 2.6: Internet Accessibility Restriction.
SSL (Secure Sockets Layer): An older encryption protocol, largely replaced by TLS in modern systems. Swift does not specify SSL for SNL-HSM communications, favoring NTLS.Conclusion: This is incorrect.
C. NTLS and Telnet
NTLS: As above, this is valid for SwiftNet communications.
Telnet: As an unencrypted protocol, it is not acceptable for securing HSM communications, perControl 2.5B.Conclusion: This is incorrect.
D. MPLS and SSL
MPLS (Multiprotocol Label Switching): A networking technology for routing, not an encryption method, and not relevant to SNL-HSM security.
SSL: As above, not used in this context by Swift.Conclusion: This is incorrect.
Step 3: Conclusion and Verification
The correct answer isA, as NTLS secures the data communication and SSH provides secure management access between the SNL host and HSM, consistent withCSCF v2024and Swift technical documentation.
References
Swift Customer Security Controls Framework (CSCF) v2024, Control 2.5B: Cryptographic Key Management, Control 2.6: Internet Accessibility Restriction.
Swift Alliance Gateway Technical Documentation, Section: Network Security Protocols.
Swift Security Best Practices, Section: HSM and SNL Configuration.
A Swift user relies on a sFTP server to connect through an externally exposed connection with a service provider or a group hub What architecture type is the Swift user? (Choose all that apply.)

A1
A2
A3
A4
The Swift Customer Security Programme (CSP) defines specific architecture types in itsCustomer Security Controls Framework (CSCF)documentation to classify how Swift users connect to the Swift network. These architecture types help determine the applicable security controls based on the user’s connectivity and infrastructure setup. The architecture types relevant to this question—A1, A2, A3, and A4—are outlined in theCSCF v2024(and prior versions like CSCF v2023), which is the latest framework as of March 06, 2025, unless superseded by a newer release.
Step 1: Understand the Scenario
The question specifies that the Swift user relies on ansFTP server(Secure File Transfer Protocol) to connect through anexternally exposed connectionwith aservice provider or a group hub. This implies that the user’s Swift environment involves external connectivity, potentially managed by a third party (service provider) or a centralized entity (group hub), rather than a fully self-managed, local setup.
Step 2: Define Swift Architecture Types
According to theSwift Customer Security Controls Framework (CSCF)and supporting documentation (e.g.,Swift Customer Security Programme – Architecture Types Explained), the architecture types are categorized as follows:
A1: Messaging Interface Only (Local Deployment)
The user operates a local Swift messaging interface (e.g., Alliance Access/Entry) with no external connectivity to a service provider or hub.
Connectivity to Swift is direct and locally managed.
A2: Messaging Interface with Connectivity Service (External Connectivity)
The user operates a local Swift messaging interface but connects to Swift via anexternally provided connectivity service(e.g., through a service provider or third-party connection).
The connection point is exposed externally to the service provider.
A3: Hosted Messaging Interface
The Swift messaging interface itself is hosted externally by a service provider, and the user accesses it remotely (e.g., via a browser or client application).
No local messaging interface exists at the user’s site.
A4: Group Hub or Shared Connectivity
The user connects to Swift via agroup hubor shared infrastructure operated by a parent entity, affiliate, or third-party provider.
This may involve centralized messaging and connectivity services shared across multiple entities.
Step 3: Analyze the Scenario Against Architecture Types
sFTP Server Usage: The use of an sFTP server suggests a file transfer mechanism, commonly employed in Swift environments to exchange payment messages or files with external parties (e.g., service providers or hubs). This aligns with scenarios where connectivity extends beyond the user’s local environment.
Externally Exposed Connection: The phrase “externally exposed connection” indicates that the Swift user’s infrastructure interfaces with an external entity (service provider or group hub), ruling out a fully self-contained setup.
Service Provider or Group Hub:
Aservice providertypically implies a third-party entity managing connectivity or hosting services, which could align withA2(external connectivity) orA3(hosted interface).
Agroup hubsuggests a shared infrastructure within a corporate group or consortium, pointing towardA4.
Step 4: Match to Architecture Types
A1: Does not apply. A1 requires a fully local deployment with no external connectivity reliance. The externally exposed sFTP connection contradicts this.
A2: Applies. If the Swift user maintains a local messaging interface (e.g., Alliance Access) and uses the sFTP server to connect to a service provider’s external infrastructure, this fits A2. The “externally exposed connection” aligns with A2’s requirement of relying on an external connectivity service.
A3: Unlikely, but possible with clarification. A3 involves a fully hosted messaging interface (e.g., no local Alliance software). The question does not explicitly state that the messaging interface is hosted externally, only that an sFTP server is used for connectivity. Without evidence of a hosted interface, A3 is not a strong fit.
A4: Applies if a group hub is involved. If the sFTP server connects to a centralized group hub (e.g., a shared Swift infrastructure within a corporate group), this matches A4. The “group hub” reference in the question supports this possibility.
Step 5: Conclusion and Verification
Based on theCSCF v2024architecture definitions and theSwift CSP Architecture Types Explainedguidance:
A2is confirmed because the sFTP server and externally exposed connection suggest reliance on a service provider for connectivity, with a local messaging interface assumed unless otherwise specified.
A4is also applicable if the “group hub” scenario is active, indicating shared connectivity infrastructure.
The question asks to “choose all that apply,” and since it specifies “service providerorgroup hub,” both A2 and A4 are valid depending on the context. However, A2 is the most universally applicable based on the sFTP and external connection details, with A4 as an additional fit for group hub cases.
References
Swift Customer Security Controls Framework (CSCF) v2024, Section: Architecture Types.
Swift Customer Security Programme – Architecture Types Explained, available via Swift’s official documentation portal (swift.com).
Swift CSP FAQ, clarifying connectivity and hosting scenarios.
In an entity having a small infrastructure and only 2 operators, the HR manager explains in a short interview how the security training is implemented providing one example. Would it be acceptable?

Yes. it's a risk based testing approach this can be enough in this case
No. more evidence are required
This question assesses whether a short interview with the HR manager providing one example of security training implementation is acceptable for a small infrastructure with only two operators, under the Swift Customer Security Programme (CSP).
Step 1: Understand Security Training Requirements
TheSwift Customer Security Controls Framework (CSCF) v2024, underControl 5.1: Security Training and Awareness, mandates that all personnel with access to Swift-related systems (including operators) receive regular, documented security training. This includes awareness of security policies, procedures, and incident response. The control applies regardless of the size of the infrastructure.
Step 2: Analyze the Scenario
The entity has a small infrastructure with two operators, and the HR manager provides a short interview with one example of security training implementation.
TheIndependent Assessment Frameworkrequires assessors to validate the effectiveness of controls, including evidence of training completion, content, frequency, and attendance records. A risk-based approach allows flexibility, but minimum evidence standards must still be met.
Step 3: Evaluate Against CSCF Guidelines
Control 5.1specifies that training must be documented, with evidence such as training logs, attendance records, or certification. A single interview with one example does not provide sufficient evidence to demonstrate:
That all operators (both in this case) have been trained.
The frequency and comprehensiveness of the training program.
The effectiveness of the training (e.g., understanding and application).
TheSwift CSP FAQandSecurity Best Practicesnote that even for small entities, assessors must see multiple pieces of evidence (e.g., training schedules, materials, test results) to confirm compliance, especially during an independent assessment.
A risk-based testing approach (mentioned in option A) allows tailoring the depth of evidence based on risk, but it does not exempt small entities from providing more than a single anecdotal example. TheIndependent Assessment Frameworkrequires objective evidence, not just verbal assurances.
Step 4: Conclusion and Verification
The answer isB, as a short interview with one example is insufficient to meet the evidence requirements ofControl 5.1in theCSCF v2024. More evidence (e.g., training records, attendance logs, or test results) is required to validate compliance, even for a small infrastructure.
References
Swift Customer Security Controls Framework (CSCF) v2024, Control 5.1: Security Training and Awareness.
Swift Independent Assessment Framework, Section: Evidence Requirements.
Swift Security Best Practices, Section: Training Documentation.
Swift CSP FAQ, Section: Small Entity Compliance.
A Swift user has moved from one Service Bureau to another What are the obligations of the Swift user in the CSP context?

To inform the SB certification office at Swift WW
To reflect that in the next attestation cycle
None if there is no impact in the architecture tope
To submit an updated attestation reflecting this change within 3 months
This question addresses the obligations of a Swift user who has switched from one Service Bureau (SB) to another under the Customer Security Programme (CSP).
Step 1: Understand CSP Obligations for Changes
TheSwift Customer Security Controls Framework (CSCF) v2024andIndependent Assessment Frameworkrequire Swift users to maintain accurate and up-to-date information regarding their infrastructure,including changes in service providers like Service Bureaus. Such changes may impact compliance and architecture types.
Step 2: Evaluate Each Option
A. To inform the SB certification office at Swift WWThere is no specific "SB certification office" mentioned in theCSCF v2024orSwift CSP Guidelines. Notifications are typically handled through attestation updates, not a dedicated office.Conclusion: Incorrect.
B. To reflect that in the next attestation cycleWhile changes must be reflected in attestations, delaying this until the next cycle (e.g., annually) is insufficient if the change affects compliance. TheSwift CSP Compliance Guidelinesrequire timely updates for significant changes.Conclusion: Incorrect.
C. None if there is no impact in the architecture typeEven if the architecture type (e.g., A2, A4) remains unchanged, a switch in Service Bureau may affect security controls, vendor management, or connectivity. TheCSCF v2024underControl 1.1: Swift Environment Protectionrequires users to report changes that could impact compliance, regardless of architecture type.Conclusion: Incorrect.
D. To submit an updated attestation reflecting this change within 3 monthsTheSwift CSP Compliance GuidelinesandIndependent Assessment Frameworkmandate that significant changes (e.g., switching Service Bureaus) be reported through an updated attestation within 3 months. This ensures Swift is informed of potential compliance impacts and allows for review.Conclusion: Correct.
Step 3: Conclusion and Verification
The correct answer isD, as theCSCF v2024andSwift CSP Compliance Guidelinesrequire an updated attestation within 3 months to reflect a change in Service Bureau.
References
Swift Customer Security Controls Framework (CSCF) v2024, Control 1.1: Swift Environment Protection.
Swift Independent Assessment Framework, Section: Change Reporting.
Swift CSP Compliance Guidelines, Section: Timely Updates.
Which of the following infrastructures has the smallest Swift footprint?

Full stack of products up to the Messaging Interface
Alliance Remote Gateway
Alliance Lite2
Full stack of products includinq IPLA
This question compares the SWIFT footprint (components within the CSP scope) across different infrastructures:
Step 1: Define SWIFT Footprint
The SWIFT footprint includes all systems and components handling SWIFT messaging or connectivity, as defined in CSCF Control 1.1 – SWIFT Environment Protection.
Which authentication methods are possible on the Alliance Interfaces? (Choose all that apply.)

Password
LDAP Authentication
Radius One-time password
Password and TOTP
This question identifies the authentication methods supported by Alliance Interfaces (e.g., Alliance Access, Alliance Gateway) under theSwift Customer Security Controls Framework (CSCF) v2024.
Step 1: Understand Authentication on Alliance Interfaces
TheCSCF v2024, underControl 2.3: System Access Control, mandates strong authentication for access to Swift-related components, including Alliance Interfaces. TheSwift Alliance Gateway Technical DocumentationandAlliance Access User Guidedetail supported methods.
Step 2: Evaluate Each Option
A. PasswordAlliance Interfaces support basic password authentication as a standard method, as noted in theAlliance Access User Guide. While not the strongest alone, it is permitted with additional controls.Conclusion: Correct.
B. LDAP AuthenticationLDAP (Lightweight Directory Access Protocol) is supported for centralized authentication, integrating with enterprise directory services, per theSwift Security Best PracticesandControl 2.3.Conclusion: Correct.
C. Radius One-time passwordRADIUS with one-time passwords (OTP) is not a standard authentication method for Alliance Interfaces. TheAlliance Gateway Technical Documentationdoes not list RADIUS OTP as supported, focusing instead on password, LDAP, and TOTP.Conclusion: Incorrect.
D. Password and TOTPTime-based One-Time Password (TOTP) combined with password (multi-factor authentication) is supported for enhanced security, as required byControl 2.3and detailed in theSwift Security Best Practicesfor privileged access.Conclusion: Correct.
Step 3: Conclusion and Verification
The correct answers areA, B, and D, as these methods are supported by Alliance Interfaces, aligning withCSCF v2024and related documentation.
References
Swift Customer Security Controls Framework (CSCF) v2024, Control 2.3: System Access Control.
Swift Alliance Gateway Technical Documentation, Section: Authentication Methods.
Swift Security Best Practices, Section: Multi-Factor Authentication.
For each of the following setups, the responsible party is identified to protect the virtualization or cloud underlying platform. Which one of the combinations is not correct?
•Swift Customer Security Controls Policy
•Swift Customer Security Controls Framework v2025
•Independent Assessment Framework
•Independent Assessment Process for Assessors Guidelines
•Independent Assessment Framework - High-Level Test Plan Guidelines
•Outsourcing Agents - Security Requirements Baseline v2025
•CSP Architecture Type - Decision tree
•CSP_controls_matrix_and_high_test_plan_2025
•Assessment template for Mandatory controls
•Assessment template for Advisory controls
•CSCF Assessment Completion Letter
•Swift_CSP_Assessment_Report_Template
For on-premises virtualization platform: by the platform provider
For virtualization platform deployed at a third party on which user’s SWIFT-related components are virtually hosted: by the third party
For on-premises container platform: by the SWIFT user
For Cloud Provider: the cloud provider
The CSCF and "Outsourcing Agents - Security Requirements Baseline v2025" define responsibilities for securing virtualization or cloud platforms hosting SWIFT-related components. Let’s evaluate each combination:
•Option A: For on-premises virtualization platform: by the platform provider
This is not correct. An on-premises virtualization platform (e.g., VMware or Hyper-V hosting Alliance Gateway) is managed by the SWIFT user, not the platform provider (e.g., VMware). The "platform provider" supplies the software, but the user is responsible for securing the on-premises environment, including hardening, patching, and compliance with CSCF Control "2.3 System Hardening."
•Option B: For virtualization platform deployed at a third party on which user’s SWIFT-related components are virtually hosted: by the third party
This is correct. If the virtualization platform is hosted by a third party (e.g., a service provider hosting SWIFT components), the third party is responsible for securing the platform, as per the "Outsourcing Agents - Security Requirements Baseline v2025" and CSCF Control "1.1."
•Option C: For on-premises container platform: by the SWIFT user
This is correct. An on-premises container platform (e.g., Docker or Kubernetes hosting SWIFT applications) is the user’s responsibility to secure, aligning with CSCF Control "1.1" and the user’s ownership of on-premises infrastructure.
•Option D: For Cloud Provider: the cloud provider
This is correct. In a cloud model (e.g., IaaS like Alliance Cloud on AWS), the cloud provider (e.g., AWS) is responsible for securing the underlying platform, as outlined in the "Outsourcing Agents - Security Requirements Baseline v2025."
Summary of Correct Answer:
The combination that is not correct is A, as the SWIFT user, not the platform provider, is responsible for securing an on-premises virtualization platform.
References to SWIFT Customer Security Programme Documents:
•Swift Customer Security Controls Framework v2025: Control 1.1 defines responsibilities for on-premises platforms.
•Outsourcing Agents - Security Requirements Baseline v2025: Specifies third-party and cloud provider responsibilities.
•Independent Assessment Framework: Confirms user responsibility for on-premises setups.
Can an internal audit department submit and approve their SWIFT user’s attestation on the KYC-SA SWIFT portal? (Select the correct answer)
•Swift Customer Security Controls Policy
•Swift Customer Security Controls Framework v2025
•Independent Assessment Framework
•Independent Assessment Process for Assessors Guidelines
•Independent Assessment Framework - High-Level Test Plan Guidelines
•Outsourcing Agents - Security Requirements Baseline v2025
•CSP Architecture Type - Decision tree
•CSP_controls_matrix_and_high_test_plan_2025
•Assessment template for Mandatory controls
•Assessment template for Advisory controls
•CSCF Assessment Completion Letter
•Swift_CSP_Assessment_Report_Template
Yes, providing this is agreed by the head of IT operations and the CISO
No, this is never an option
Yes, an internal auditor can submit the attestation for approval provided they have the appropriate credentials for swift.com. The CISO remains in charge of the approval of the attestation
Yes, with approval from the Chief Auditor
The "Independent Assessment Framework" and "Independent Assessment Process for Assessors Guidelines" mandate that CSP assessments and attestations be conducted by an independent, certified assessor, not the user’s internal audit department. Let’s evaluate each option:
•Option A: Yes, providing this is agreed by the head of IT operations and the CISO
This is incorrect. Internal agreement does not override the CSP’s requirement for independence.
•Option B: No, this is never an option
This is correct. The CSP prohibits internal audit departments from submitting or approving attestations on the KYC-SA portal, as they lack the independence required by the "Independent Assessment Framework." Only an external, certified assessor can perform and approve the assessment, with the CISO or designated user submitting the attestation based on the assessor’s report.
•Option C: Yes, an internal auditor can submit the attestation for approval provided they have the appropriate credentials for swift.com. The CISO remains in charge of the approval of the attestation
This is incorrect. Internal auditors cannot submit or approve attestations, even with credentials, due to the independence requirement.
•Option D: Yes, with approval from the Chief Auditor
This is incorrect. Chief Auditor approval does not satisfy the CSP’s independence mandate.
Summary of Correct Answer:
An internal audit department cannot submit or approve the attestation (B).
References to SWIFT Customer Security Programme Documents:
•Independent Assessment Framework: Requires independent assessors.
•Independent Assessment Process for Assessors Guidelines: Prohibits internal assessments for attestation.
•Swift_CSP_Assessment_Report_Template: Specifies external assessor input.
========
Which operator session flows are expected to be protected in terms of confidentiality and integrity? (Choose all that apply.)

System administrator sessions towards a host running a Swift related component
All sessions to and from a jump server used to access a component in a secure zone
All sessions towards a secure zone (on-premises or hosted by a third-party or a Cloud Provider)
All sessions towards a Swift related application run by an Outsourcing Agent, a Service Bureau or an L2BA Provider
This question addresses the obligations of Swift users regarding the submission of assessment-related documents to Swift under the Customer Security Programme (CSP).
Step 1: Understand CSP Assessment Submission Requirements
TheSwift Customer Security Controls Framework (CSCF) v2024and theIndependent Assessment Frameworkoutline the process for CSP assessments, including what must be submitted to Swift. The focus is on ensuring compliance through attestation, with specific deliverables defined.
Step 2: Evaluate Each Option
A. Yes, all documents produced from the assessment must be provided proactively to SwiftThis is incorrect. TheIndependent Assessment Frameworkdoes not require proactive submission of all assessment documents (e.g., detailed reports, working papers). Only the completion letter and attestation are typically submitted unless otherwise requested by Swift.Conclusion: Incorrect.
B. No, it is not required to provide Swift with any documents by default. However, Swift can request a copy of the Assessment completion letterTheCSCF v2024andIndependent Assessment Frameworkstate that users are not required to proactively submit the full assessment report or other documents. However, Swift retains the right to request the completion letter (certifying assessment completion) or additional evidence during quality assurance reviews. This aligns with theSwift CSP Compliance Guidelines.Conclusion: Correct.
C. Yes, a copy of (only) the assessment report must be provided to Swift, no other documentsThis is incorrect. The full assessment report is not mandated for proactive submission; only the completion letter is typically required unless requested. TheIndependent Assessment Frameworkemphasizes the completion letter as the key deliverable.Conclusion: Incorrect.
D. Yes, in cases where a customer performs an Independent assessment rather than an audit then a copy of the assessment report must be provided. However, it is not required for the Swift user to provide any forms when an Internal/External Audit is performedThis is partially misleading. TheIndependent Assessment Frameworkdoes not distinguish between independent assessments and audits in terms of mandatory report submission. For both, the completion letter is the default submission, with reports requested only if needed. The differentiation based on assessment type is not supported byCSCF v2024guidelines.Conclusion: Incorrect.
Step 3: Conclusion and Verification
The correct answer isB, as theCSCF v2024andIndependent Assessment Frameworkdo not require proactive submission of the full assessment report, but Swift can request the completion letter as part of its oversight process.
References
Swift Customer Security Controls Framework (CSCF) v2024, Section: Independent Assessment Requirements.
Swift Independent Assessment Framework, Section: Deliverables and Submission.
Swift CSP Compliance Guidelines, Section: Document Submission Rules.
=========================
This question identifies which operator session flows must be protected for confidentiality and integrity under theSwift Customer Security Controls Framework (CSCF) v2024.
Step 1: Understand Session Protection Requirements
TheCSCF v2024, underControl 2.4: Secure Session Management, mandates that all sessions involving access to Swift-related components or secure zones must be protected using strong encryption (e.g., TLS) and integrity controls to prevent unauthorized access or data tampering. This applies to operator and administrator sessions interacting with the Swift environment.
Step 2: Evaluate Each Option
A. System administrator sessions towards a host running a Swift related componentAdministrator sessions to hosts running Swift components (e.g., Alliance Access, Gateway) are in scope, as they require protection perControl 2.4to ensure confidentiality and integrity of administrative actions.Conclusion: Correct.
B. All sessions to and from a jump server used to access a component in a secure zoneJump servers are used to access secure zones (perControl 1.1: Swift Environment Protection), and all sessions to and from them must be encrypted and integrity-protected, as specified inControl 2.4.Conclusion: Correct.
C. All sessions towards a secure zone (on-premises or hosted by a third-party or a Cloud Provider)Secure zones, whether on-premises or hosted (e.g., by outsourcing agents or cloud providers), contain Swift components and must have all incoming sessions protected perControl 2.4andControl 1.1.Conclusion: Correct.
D. All sessions towards a Swift related application run by an Outsourcing Agent, a Service Bureau or an L2BA ProviderSessions to Swift-related applications managed by outsourcing agents or service bureaus (e.g., Components C, D, E in the diagram) are in scope, as they handle Swift traffic and must be secured perControl 2.4and theSwift Outsourcing Guidelines.Conclusion: Correct.
Step 3: Conclusion and Verification
All options (A, B, C, D) are correct, asControl 2.4of theCSCF v2024requires protection of all listed session types to ensure confidentiality and integrity across the Swift ecosystem, including secure zones, hosted environments, and outsourced applications.
References
Swift Customer Security Controls Framework (CSCF) v2024, Control 2.4: Secure Session Management, Control 1.1: Swift Environment Protection.
Swift Security Best Practices, Section: Session Security.
Swift Outsourcing Guidelines, Section: Session Protection.
In the illustration, identify which components are in scope of the CSCF? (Choose all that apply.)

Components A, B, K
Components J, K, I
Components F, G, H
Components C, E, M
The Swift Customer Security Controls Framework (CSCF) defines the scope of components that must comply with its security controls. This scope is detailed in theCSCF v2024(and prior versions like CSCF v2023), which specifies that the CSCF applies to systems directly involved in the Swift messaging and connectivity ecosystem. Let’s analyze the diagram to identify which components fall within this scope.
Step 1: Understand the Scope of CSCF
According to theSwift Customer Security Controls Framework (CSCF) v2024, the scope includes:
Swift messaging interfaces(e.g., Alliance Access/Entry, RMA).
Communication interfacesto the Swift network (e.g., SNL, HSM, PKI).
Operator systemsdirectly interacting with Swift components (e.g., GUIs, admin/operator workstations).
Middlewareor connectors directly facilitating Swift message flows.Systems that are not directly involved in Swift messaging or connectivity (e.g., back-office systems, general-purpose servers) are typically out of scope unless they pose a direct risk to the Swift environment.
Step 2: Analyze the Diagram and Identify Components
The diagram includes the following labeled components:
A. Back Office: A system for back-office operations, not directly part of Swift messaging.
B. Back Office Using Middleware Client: A back-office system with middleware for data exchange.
C. Messaging Interface: Likely a Swift messaging interface (e.g., Alliance Access).
D. RMA: Relationship Management Application, a Swift component for managing messaging relationships.
E. GUI: Graphical User Interface for operators to interact with the messaging interface.
F. Communication Interface: Interface for connecting to the Swift network.
G. SNL: SwiftNet Link, a communication layer for Swift connectivity.
H. HSM & PKI: Hardware Security Module and Public Key Infrastructure, used for secure Swift connectivity.
I. Middleware File Transfer Servers: Servers facilitating data exchange between back-office and Swift systems.
J, K, L. Data Exchange Paths: Represent data flows between systems (not components themselves).
M. Operator (End User): The operator’s workstation interacting with the Swift GUI.
N. Connector: The connection point to the Swift network.
Step 3: Evaluate Each Option Against CSCF Scope
A. Components A, B, K
A (Back Office): Back-office systems are not in scope unless they directly process Swift messages. The CSCF focuses on Swift-specific infrastructure, and back-office systems are typically considered out of scope unless they pose a direct risk (e.g., via middleware).
B (Back Office Using Middleware Client): While this system uses middleware to exchange data with Swift components, it is still a back-office system, not a core Swift component. The middleware itself (I) may be in scope, but the client (B) is not.
K (Data Exchange Path): This is a data flow, not a component, and thus not directly in scope.Conclusion: This option is incorrect.
B. Components J, K, I
J, K (Data Exchange Paths): These are data flows, not components, and are not directly in scope.
I (Middleware File Transfer Servers): Middleware that facilitates Swift message flows (e.g., between back-office and messaging interface) can be in scope if it directlyprocesses or transmits Swift messages. PerControl 1.1: Swift Environment Protection, middleware in the Swift data flow must be secured, making it in scope. However, this option pairs I with J and K, which are not components.Conclusion: This option is incorrect due to J and K, though I alone would be in scope.
C. Components F, G, H
F (Communication Interface): This is the interface connecting to the Swift network, clearly in scope perControl 1.1.
G (SNL): SwiftNet Link is a core communication component for Swift connectivity, in scope perControl 1.1.
H (HSM & PKI): HSM and PKI are critical for secure Swift connectivity, in scope perControl 1.1.Conclusion: This option is correct.
D. Components C, E, M
C (Messaging Interface): This is a core Swift component (e.g., Alliance Access), in scope perControl 1.1.
E (GUI): The GUI used by operators to interact with the messaging interface is in scope, as specified inControl 1.2: Logical Access Control, which includes operator systems.
M (Operator End User): The operator’s workstation is in scope as it directly interacts with Swift systems, perControl 1.2.Conclusion: This option is correct.
Step 4: Conclusion and Verification
The components in scope of the CSCF are those directly involved in Swift messaging, connectivity, and operator interaction. Based on the analysis:
C (F, G, H)includes communication components, all in scope.
D (C, E, M)includes the messaging interface, GUI, and operator workstation, all in scope.Components A, B, and data exchange paths (J, K, L) are not directly in scope, though middleware (I) would be if considered separately.
References
Swift Customer Security Controls Framework (CSCF) v2024, Control 1.1: Swift Environment Protection.
Swift Customer Security Programme – Scope and Applicability, Section: CSCF Scope Definition.
CSCF v2024, Control 1.2: Logical Access Control.
What type of keys does the HSM box store? (Select the correct answer)
•Connectivity
•Generic
•Products Cloud
•Products OnPrem
•Security
Private keys
Public keys
Both private and public keys
A Hardware Security Module (HSM) box in the SWIFT context is a secure device used to manage cryptographic keys and perform security operations, such as signing and encryption for SWIFT transactions. Let’s evaluate each option:
•Option A: Private keys
This is correct. The primary function of an HSM box in the SWIFT environment is to securely store and manage private keys, which are part of the Public Key Infrastructure (PKI) used for asymmetric cryptography. Private keys are used for signing messages to ensure authenticity and integrity, and for decryption to maintain confidentiality. The HSM protects these private keys from unauthorized access, aligning with CSCF Control "1.3 Cryptographic Failover," which mandates the use of HSMs to safeguard cryptographic materials. SWIFT documentation specifies that private keys are stored within the HSM, while public keys are distributed separately (e.g., via certificates).
•Option B: Public keys
This is incorrect. Public keys are not stored in the HSM box. Instead, they are embedded in PKI certificates and distributed to other parties (e.g., SWIFT or counterparties) for verification and encryption purposes. The HSM’s role is to protect the sensitive private keys, not to store public keys, which are openly shared as part of the PKI ecosystem.
•Option C: Both private and public keys
This is incorrect. While the HSM may temporarily handle public keys during cryptographic operations (e.g., for certificate validation), its primary and secure storage function is limited to private keys. Storing both types of keys is not a standard practice in SWIFT’s HSM usage, as public keys are managed outside the HSM in certificate repositories or directories.
Summary of Correct Answer:
The HSM box stores private keys (A), ensuring the security of cryptographic operations in the SWIFT environment.
References to SWIFT Customer Security Programme Documents:
•SWIFT Customer Security Controls Framework (CSCF) v2024: Control 1.3 mandates HSMs for storing private keys securely.
•SWIFT Security Guidelines: Details the HSM’s role in managing private keys for PKI operations.
•SWIFT HSM Documentation: Confirms that private keys are stored in the HSM, with public keys managed externally.
========
Select the correct statement(s).

The public and private keys of a Swift certificate are stored on the Hardware Security Module
The certificate stored on the Swift Hardware Security Module is used during the decryption operation of a message
The decryption operation uses the encryption private key of the receiver
To verify the signature the SwiftNetLink uses the signing private key of the receiver
This question involves the role of the Hardware Security Module (HSM) and cryptographic operations in the Swift environment. Let’s evaluate each option.
Step 1: Understand HSM and Cryptographic Operations in Swift
The HSM is a secure device used to manage cryptographic keys and perform encryption/decryption operations, as detailed inControl 2.5B: Cryptographic Key Managementof theCSCF v2024. Swift uses public key infrastructure (PKI) for secure messaging, with HSMs storing keys and certificates.
Step 2: Evaluate Each Option
A. The public and private keys of a Swift certificate are stored on the Hardware Security ModuleIn the Swift environment, the HSM stores both the private key (for signing/decryption) and the public key (for verification/encryption) as part of the certificate pair. This is a standard practice for secure key management, as confirmed in theSwift Security Best PracticesandControl 2.5B, which mandates secure storage of cryptographic keys in HSMs.Conclusion: This statement is correct.
B. The certificate stored on the Swift Hardware Security Module is used during the decryption operation of a messageThe HSM uses the private key stored in the certificate to perform decryption of incoming Swift messages. This is part of the secure message handling process, as outlined inControl 2.5Band theSwift Alliance Gateway Technical Documentation.Conclusion: This statement is correct.
C. The decryption operation uses the encryption private key of the receiverDecryption uses theprivate keyof the receiver, not the “encryption private key” (a misnomer). The correct term is the receiver’s private key, which corresponds to the public key used for encryption. This error makes the statement technically incorrect, despite the intended meaning.Conclusion: This statement is incorrect.
D. To verify the signature the SwiftNetLink uses the signing private key of the receiverSignature verification requires the sender’s public key, not the receiver’s private key. The SwiftNetLink (SNL) uses the public key to verify the signature, as perControl 2.5BandSwift Security Best Practices. The private key is used for signing, not verification.Conclusion: This statement is incorrect.
Step 3: Conclusion and Verification
The verified statements areAandB, as they accurately describe the HSM’s role in key storage and decryption, consistent with Swift CSP documentation.
References
Swift Customer Security Controls Framework (CSCF) v2024, Control 2.5B: Cryptographic Key Management.
Swift Security Best Practices, Section: HSM Usage.
Swift Alliance Gateway Technical Documentation, Section: Cryptographic Operations.
A Swift user has remediated an exception reported by the assessor. What are their obligations before updating and submitting an attestation reflecting the new compliance level?

The exception must be re-assessed by an independent assessor. The assessor can be different to the one who initially raised the exception
The exception must be re-assessed by the same independent assessor that raised the exception
The first line of defense can confirm their level of compliance using a self-assessment approach
None, if the remediation has been completed, a new attestation can be submitted reflecting the compliance of the control
This question explores the process for updating an attestation after remediating an exception identified by an assessor:
Step 1: CSP Attestation and Remediation Process
The SWIFT CSP requires users to submit an annual attestation via the KYC Security Attestation (KYC-SA) application, reflecting compliance with CSCF controls. If anexception (non-compliance) is reported, remediation must occur, followed by validation before updating the attestation.
Copyright © 2014-2025 Examstrust. All Rights Reserved
