Which two criteria should an administrator use when defining Location Awareness for the Symantec Endpoint Protection (SEP) client? (Select two.)
Why does Power Eraser need Internet access?
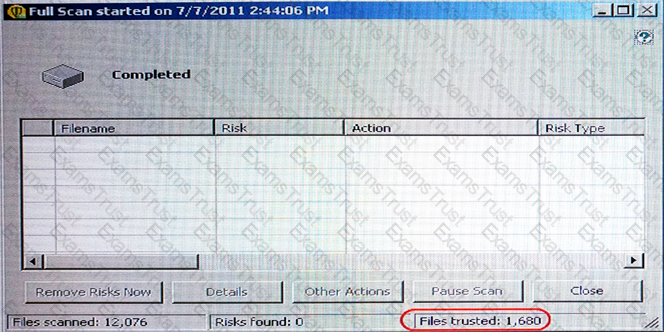
Which settings can impact the Files trusted count?
A company has 10,000 Symantec Endpoint Protection (SEP) clients deployed using two Symantec Endpoint Protection Managers (SEPMs).
Which configuration is recommended to ensure that each SEPM is able to effectively handle the communications load with the SEP clients?
Which action can an administrator take to improve the Symantec Endpoint Protection Manager (SEPM) dashboard performance and report accuracy?
A Symantec Endpoint Protection (SEP) administrator creates a firewall policy to block FTP traffic and assigns the policy to all of the SEP clients. The network monitoring team informs the administrator that a client system is making an FTP connection to a server. While investigating the problem from the SEP client GUI, the administrator notices that there are zero entries pertaining to FTP traffic in the SET Traffic log or Packet log. While viewing the Network Activity dialog, there is zero inbound/outbound traffic for the FTP process.
What is the most likely reason?
Which two are policy types within the Symantec Endpoint Protection Manager? (Select two.)
A company has a small number of systems in their Symantec Endpoint Protection Manager (SEPM) group with federal mandates that AntiVirus definitions undergo a two week testing period. After being loaded on the client, the tested virus definitions must remain unchanged on the client systems until the next set of virus definitions have completed testing. All other clients must remain operational on the most recent definition sets. An internal LiveUpdate Server has been considered as too expensive to be a solution for this company.
What should be modified on the SEPM to meet this mandate?
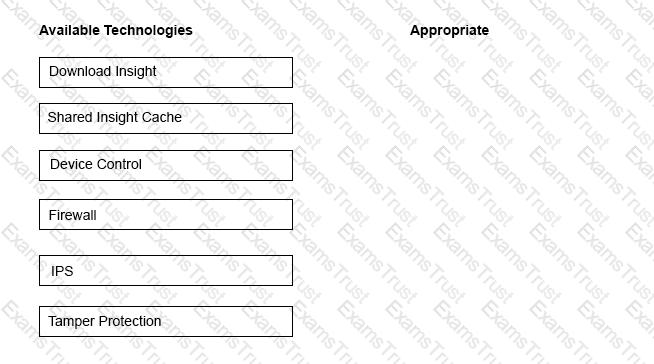
An administrator is unknowingly trying to connect to a malicious website and download a known threat within a .rar file. All Symantec Endpoint Protection technologies are installed on the client’s system.
Drag and drop the technologies to the right side of the screen in the sequence necessary to block or detect the malicious file.
A company needs to configure an Application and Device Control policy to block read/write access to all USB removable media on its Symantec Endpoint Protection (SEP) systems.
Which tool should an administrator use to format the GUID and device IDs as required by SEP?
You have just started a relayout operation in a live test environment, and you want to limit the impact of your work on concurrent testing activities. You also want to accommodate the need to constrain a relayout job’s performance impact on concurrent activities.
What would you do to perform this task?
The LiveUpdate Download Schedule is set to the default on the Symantec Endpoint Protection Manager (SEPM).
How many content revisions must the SEPM keep to ensure clients that check in to the SEPM every 10 days receive delta content packages instead of full content packages?
A Symantec Endpoint Protection administrator is using System Lockdown in blacklist mode with a file fingerprint list. When testing a client, the administrator notices that at least one of the files on the list is allowed to execute.
What is the likely cause of the problem?
Which two criteria can an administrator use to determine hosts in a host group? (Select two.)
Which Symantec Endpoint Protection technology blocks a downloaded program from installing browser plugins?
Which two criteria are used by Symantec Insight to evaluate binary executables? (Select two.)
A Symantec Endpoint Protection (SEP) administrator performed a disaster recovery without a database backup.
In which file should the SEP administrator add “scm.agent.groupcreation=true” to enable the automatic creation of client groups?
After several failed logon attempts, the Symantec Endpoint Protection Manager (SEPM) has locked the default admin account. An administrator needs to make system changes as soon as possible to address an outbreak, but the admin account is the only account.
Which action should the administrator take to correct the problem with minimal impact to the existing environment?
An organization needs to add a collection of DNS host names to permit in the firewall policy.
How Should the SEP Administrator add these DNS host names as a single rule in the firewall policy?
Which two items should an administrator enter in the License Activation Wizard to activate a license? (Select two.)