The screenshot is from Wireshark, a network protocol analyzer, displaying captured network traffic. The relevant columns include the source and destination IP addresses, ports, protocol, and additional information about the packets. Let’s break down the details:
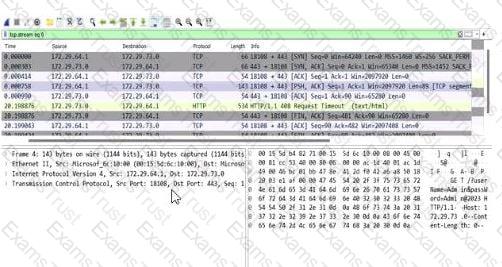
Destination Port Analysis:The screenshot shows multiple packets with a destination port of 443 (e.g., in the "Destination" column, entries like "172.72.61.9:443"). Port 443 is the default port for HTTPS (HTTP Secure), which is HTTP traffic encrypted using SSL/TLS. This indicates that the application is communicating over HTTPS.
Protocol Analysis:The "Protocol" column lists "TLSv1.2" for most packets (e.g., frame numbers 2000084, 2000086). TLS (Transport Layer Security) is the cryptographic protocol used by HTTPS to secure HTTP communications. This confirms that the traffic is HTTPS, not plain HTTP.
Packet Details:The "Info" column provides additional context, such as "Application Data" for TLS packets, indicating encrypted application-layer data (typical of HTTPS). There are also HTTP packets (e.g., frame 2000088), but these are likely part of the HTTPS session (e.g., HTTP/2 over TLS, as noted by "HTTP2").
Now, let’s evaluate the options:
Option A: "The application is running on port 443 and the HTTPS protocol."This is correct. The destination port 443 and the use of TLSv1.2 confirm that the application is using HTTPS. HTTPS is the standard protocol for secure web communication, and port 443 is its designated port. CNSP documentation emphasizes that HTTPS traffic on port 443 indicates a secure application-layer protocol, often used for web applications handling sensitive data.
Option B: "The credentials have been submitted over the HTTP protocol."This is incorrect. HTTP typically uses port 80, but the screenshot shows traffic on port 443 with TLS, indicating HTTPS. Credentials submitted over this connection would be encrypted via HTTPS, not sent in plaintext over HTTP. CNSP highlights the security risks of HTTP for credential submission due to lack of encryption, which isn’t the case here.
Option C: "The credentials have been submitted over the HTTPS protocol."While this statement could be true (since HTTPS is in use, any credentials would likely be submitted securely), the question asks for the "correct" statement based on the screenshot. The screenshot doesn’t explicitly show credential submission (e.g., a POST request withform data); it only shows the protocol and port. Option A is more directly supported by the screenshot as it focuses on the application’s protocol and port, not the specific action of credential submission. CNSP notes that HTTPS ensures confidentiality, but this option requires more specific evidence of credentials.
Option D: "The application is running on port 80 and the HTTP protocol."This is incorrect. Port 80 is the default for HTTP, but the screenshot clearly shows port 443 and TLS, indicating HTTPS. CNSP documentation contrasts HTTP (port 80, unencrypted) with HTTPS (port 443, encrypted), making this option invalid.
Conclusion:Option A is the most accurate and comprehensive statement directly supported by the screenshot, confirming the application’s use of port 443 and HTTPS. While Option C might be true in a broader context, it’s less definitive without explicit evidence of credential submission in the captured packets.
References:CNSP "Network Traffic Analysis" (Section on Protocol Identification) explains that port 443 with TLS indicates HTTPS, and contrasts it with HTTP on port 80. The "Wireshark Analysis" section further details how to interpret destination ports and protocol fields for identifying application-layer protocols.