Your organization would like to implement a mechanism to alert administrators when files on a protected servers are modified or tampered with. Which Deep Security Protection Module should you enable to provide this functionality?
What is the purpose of the override.properties file?
Which Protection Modules can make use of a locally installed Smart Protection Server?
Which of the following are valid methods for pre-approving software updates to prevent Ap-plication Control Events from being triggered by the execution of the modified software? Select all that apply.
Which of the following statements is false regarding Firewall rules using the Bypass action?
What is the result of performing a Reset operation on a Deep Security Agent?
An administrator attempts to activate the Deep Security Agent installed on a server by typing the following command in the Command Prompt on the Deep Security Agent computer:
dsa_control -a dsm://server1.acme.com:4120
The Agent does not activate as expected. What is a valid reason for this issue?
Which of the following statements is true regarding Deep Security Relays?
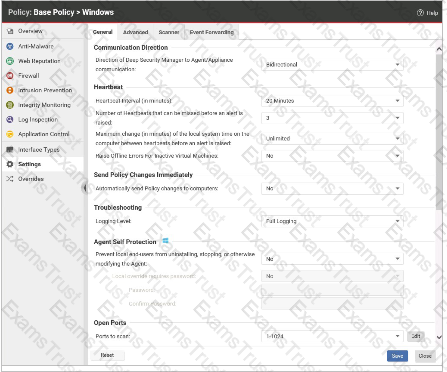
Based on the policy configuration displayed in the exhibit, which of the following statements is true?
How can you prevent a file from being scanned for malware?
Which of the following correctly describes the Firewall rule Action of Force Allow?
What is the role of Apex Central in the Connected Threat Defense infrastructure?