Which two tools are used for centralized logging in VMware NSX? (Choose two.)
Which troubleshooting step will resolve an error with code 1001 during the configuration of a time-based firewall rule?
Which two statements describe the characteristics of an Edge Cluster in NSX? (Choose two.)
An NSX administrator has deployed a single NSX Manager node and will be adding two additional nodes to form a 3-node NSX Management Cluster for a production environment. The administrator will deploy these two additional nodes and Cluster VIP using the NSX UI.
What two are the prerequisites for this configuration? (Choose two.)
An administrator has been tasked with implementing the SSL certificates for the NSX Manager Cluster VIP.
Which is the correct way to implement this change?
The security administrator turns on logging for a firewall rule.
Where is the log stored on an ESXi transport node?
Which two statements are true about IDS Signatures? (Choose two.)
Which two BGP configuration parameters can be configured in the VRF Lite gateways? (Choose two.)
Which three DHCP Services are supported by NSX? (Choose three.)
Which two statements are true for IPSec VPN? (Choose two.)
Which two choices are solutions offered by the VMware NSX portfolio? (Choose two.)
Which two of the following features are supported for the Standard NSX Application Platform Deployment? (Choose two.)
How is the RouterLink port created between a Tier-1 Gateway and Tier-O Gateway?
When a stateful service is enabled for the first lime on a Tier-0 Gateway, what happens on the NSX Edge node'
An NSX administrator Is treating a NAT rule on a Tler-0 Gateway configured In active-standby high availability mode. Which two NAT rule types are supported for this configuration? (Choose two.)
Where in the NSX UI would an administrator set the time attribute for a time-based Gateway Firewall rule?
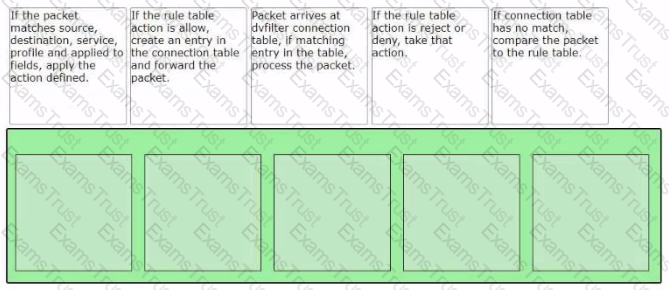
Sort the rule processing steps of the Distributed Firewall. Order responses from left to right.
An administrator has deployed 10 Edge Transport Nodes in their NSX Environment, but has forgotten to specify an NTP server during the deployment.
What is the efficient way to add an NTP server to all 10 Edge Transport Nodes?
NSX improves the security of today's modern workloads by preventing lateral movement, which feature of NSX can be used to achieve this?
A company security policy requires all users to log Into applications using a centralized authentication system.
Which two authentication, authorization, and accounting (AAA) systems are available when Integrating NSX with VMware Identity Manager? (Choose two.)
Which command is used to set the NSX Manager's logging-level to debug mode for troubleshooting?
Which two CLI commands could be used to see if vmnic link status is down? (Choose two.)
Which NSX CLI command is used to change the authentication policy for local users?
Refer to the exhibits.
Drag and drop the NSX graphic element icons on the left found in an NSX Intelligence visualization graph to Its correct description on the right.

Which two steps must an NSX administrator take to integrate VMware Identity Manager in NSX to support role-based access control? (Choose two.)
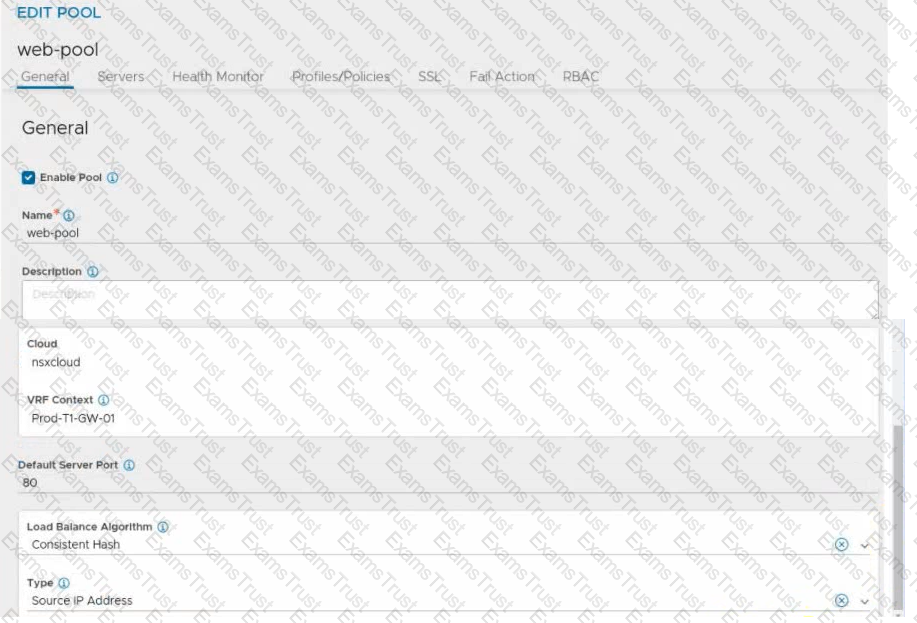
Refer to the exhibit.
An administrator configured NSX Advanced Load Balancer to redistribute the traffic between the web servers. However, requests are sent to only one server
Which of the following pool configuration settings needs to be adjusted to resolve the problem? Mark the correct answer by clicking on the image.
An NSX administrator would like to create an L2 segment with the following requirements:
• L2 domain should not exist on the physical switches.
• East/West communication must be maximized as much as possible.
Which type of segment must the administrator choose?
Which two commands does an NSX administrator use to check the IP address of the VMkernel port for the Geneve protocol on the ESXi transport node? (Choose two.)
An architect receives a request to apply distributed firewall in a customer environment without making changes to the network and vSphere environment. The architect decides to use Distributed Firewall on VDS.
Which two of the following requirements must be met in the environment? (Choose two.)
Which of the following settings must be configured in an NSX environment before enabling stateful active-active SNAT?
What are two valid options when configuring the scope of a distributed firewall rule? (Choose two.)
Which three data collection sources are used by NSX Network Detection and Response to create correlations/Intrusion campaigns? (Choose three.)