Which two steps must an NSX administrator take to integrate VMware Identity Manager in NSX to support role-based access control? (Choose two.)
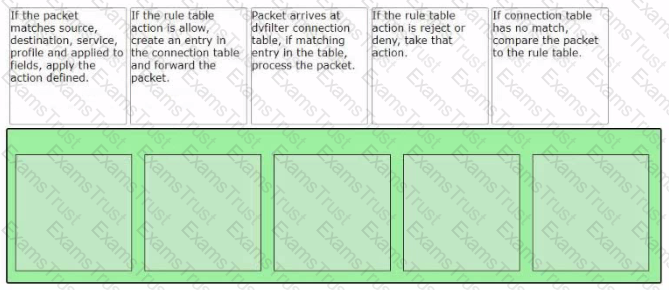
Sort the rule processing steps of the Distributed Firewall. Order responses from left to right.
Which CLI command shows syslog on NSX Manager?
Which two tools are used for centralized logging in VMware NSX? (Choose two.)
Which troubleshooting step will resolve an error with code 1001 during the configuration of a time-based firewall rule?
Which two choices are solutions offered by the VMware NSX portfolio? (Choose two.)
Which two statements are true about IDS Signatures? (Choose two.)
A company security policy requires all users to log into applications using a centralized authentication system.
Which two authentication, authorization, and accounting (AAA) systems are available when integrating NSX with VMware Identity Manager? (Choose two.)
Which CLI command on NSX Manager and NSX Edge is used to change NTP settings?
Which of the following exist only on Tler-1 Gateway firewall configurations and not on Tier-0?
What is the VMware recommended way to deploy a virtual NSX Edge Node?
A security administrator needs to configure a firewall rule based on the domain name of a specific application.
Which field in a distributed firewall rule does the administrator configure?
What should an NSX administrator check to verify that VMware Identity Manager integration is successful?
Which two are requirements for FQDN Analysis? (Choose two.)
A customer has a network where BGP has been enabled and the BGP neighbor is configured on the Tier-0 Gateway. An NSX administrator used the get gateways command to retrieve this information:

Which two commands must be executed to check BGP neighbor status? (Choose two.)
Which two built-in VMware tools will help identify the cause of packet loss on VLAN Segments? (Choose two.)
Which two built-in VMware tools will help identify the cause of packet loss on VLAN Segments? (Choose two.)
Which of the following settings must be configured in an NSX environment before enabling stateful active-active SNAT?
What are two valid BGP Attributes that can be used to influence the route path traffic will take? (Choose two.)
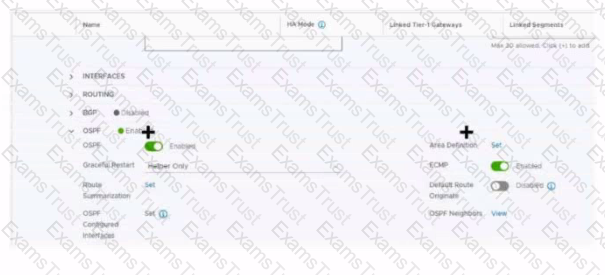
Refer to the exhibit.
Which two items must be configured to enable OSPF for the Tler-0 Gateway in the Image? Mark your answers by clicking twice on the image.
An administrator needs to download the support bundle for NSX Manager.
Where does the administrator download the log bundle from?
Which two of the following parameters are required for deploying the NSX Application Platform? (Choose two.)
In an NSX environment, an administrator is observing low throughput and congestion between the Tier-0 Gateway and the upstream physical routers.
Which two actions could address low throughput and congestion? (Choose two.)
What is the most restrictive NSX built-in role which will allow a user to apply configuration changes on an NSX Edge?
Which TraceFlow traffic type should an NSX administrator use for validating connectivity between App and DB virtual machines that reside on different segments?
What needs to be configured on a Tier-0 Gateway to make NSX Edge Services available to a VM on a VLAN-backed logical switch?
Which three of the following describe the Border Gateway Routing Protocol (BGP) configuration on a Tier-0 Gateway? (Choose three.)
Which of the two following characteristics about NAT64 are true? (Choose two.)
Which NSX CLI command is used to change the authentication policy for local users?
An NSX administrator would like to create an L2 segment with the following requirements:
• L2 domain should not exist on the physical switches.
• East/West communication must be maximized as much as possible.
Which type of segment must the administrator choose?
What are four NSX built-in role-based access control (RBAC) roles? (Choose four.)
An administrator has been tasked with implementing the SSL certificates for the NSX Manager Cluster VIP.
Which is the correct way to implement this change?
Which VPN type must be configured before enabling an L2VPN?
Which two statements are true for IPSec VPN? (Choose two.)
An NSX administrator is creating a Tier-1 Gateway configured in Active-Standby High Availability Mode. In the event of node failure, the failover policy should not allow the original failed node to become the Active node upon recovery.
Which failover policy meets this requirement?